1 Introduction
Building the infrastructure for digital identity presents challenges of verifiability, interoperability, and speed. But in light of recent data breaches and rising awareness of the need for data protection, consumers are searching for ways to retain full control over their identity data, and businesses are searching for ways to remain compliant with developing data protection frameworks.
Typically each institution that requires a user account has its own identity process. Individuals then seek out ways to create interoperability between accounts and create a honeypot of identity data that could be compromised by an attack or data breach. Institutions and businesses that interact with digital identities bear the risk of a user’s poor identity access management, and should have a strong incentive to create secure interoperability for their users.
The authenticity of identity instruments must be verified with the correct information and source. Confirming this digitally is challenging because physical identity instruments have been designed with characteristics that enable them to be verified in the real world. Digital identity instruments have not been standardized to provide this, often relegating such documents to be sent in unsecure, unverifiable forms – such as emailing a scan of a passport – or simply restricted from digital processes.
An identity trust fabric (ITF) is required for any decentralized digital identity solution. Blockchain is considered a suitable ITF and multiple projects are under development. Blockchain for decentralized identity can strengthen a user’s privacy by returning control to the individual, address data integrity of digital documents, and provide resiliency against attacks.
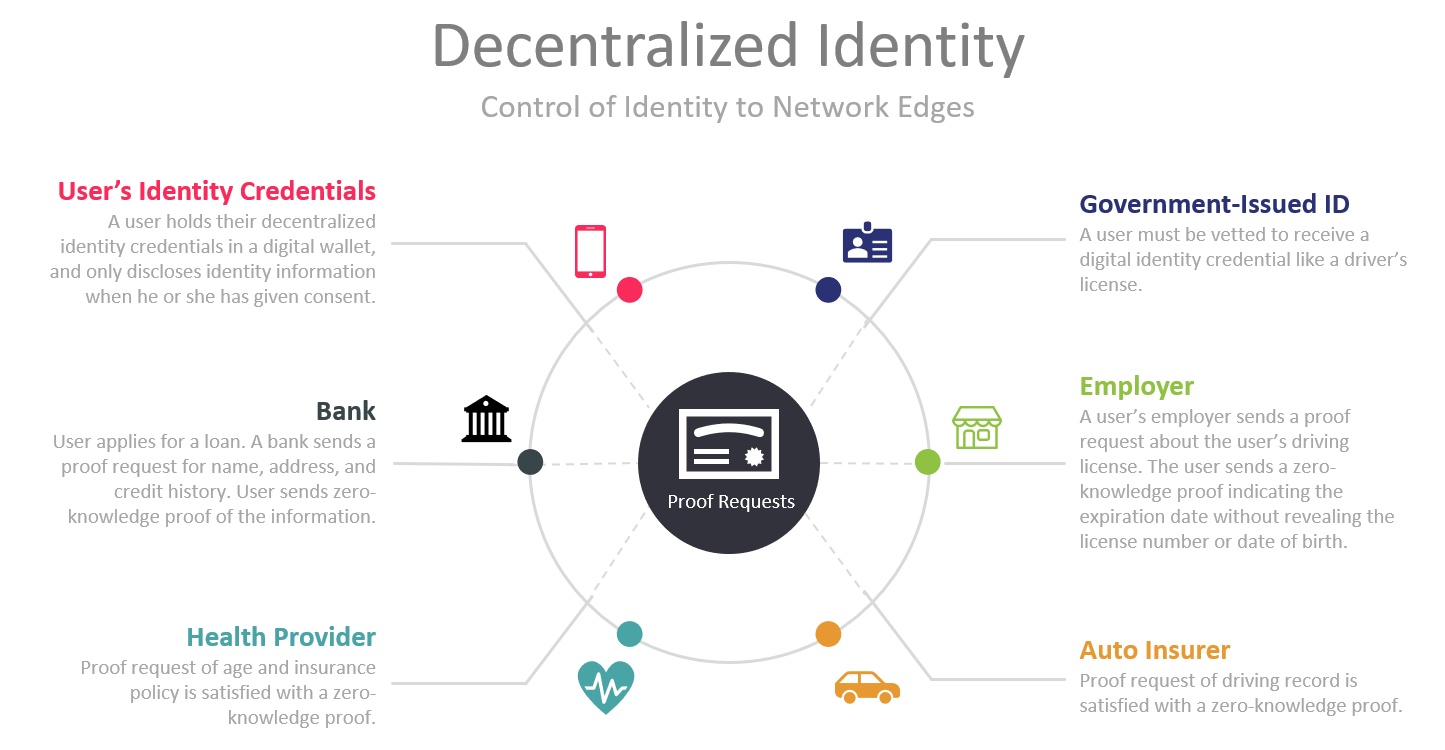
Blockchains can facilitate the secure sharing of digital identity between a user and an institution with decentralized public key infrastructure (dPKI). A user stores a digital identity in an identity wallet. When the user wants to access a service – for example to open a bank account – the user can send the public key of their digital identity to the bank as a hash. The hash displays cryptographic proof that the identity is authentic without revealing any sensitive data. The bank receives it, and because the identity has been verified at the initial entrance to the blockchain and verified at each subsequent block that was published, the bank is able to trust it.
Decentralized identity allows users to control the privacy of their identity, including minimal, selective, or progressive disclosure of their identity data to any party. Private key and all PII data remains off-chain. Blockchain addresses the integrity of data – sent in hash form – though its consensus mechanism. Cryptographically, it is impossible to send a different identity instrument than the hash specifies, or one that has been tampered with. In order for this process to be reliable, the initial registering of an identity in such a decentralized identity system must be correct, valid, and without errors.
Key challenges that drive the need for decentralized digital identity are:
- Consumer Pain Pont: When new accounts are opened, the account holder must share more information with the institution than is necessary.
- Consumer Pain Point: Consumers have little control over who has their personal information, and do not know when institutions share their identity with other institutions.
- Institutional Pain Point: Institutions are honeypots for identity data, at risk of data breach.
- Institutional Pain Point: Initiating new accounts is inefficient, relying on manual checks, postal delivery, and the customer’s own unreliable habits.
- Institutional Pain Point: Vulnerable populations such as refugees or homeless individuals often do not have physical documentation of their identity, posing a significant cost to public institutions.
Key regulatory and operational requirements that are associated with decentralized digital identity are:
- Regulation: GDPR compliance requires that all institutions protect PII data and a citizen’s right to be forgotten. Blockchain best practice dictates that only a hash of PII data is stored on-chain.
- Regulation: Nonprofit networks are developing international standards for decentralized identity solutions. Standards are under development and will continue to change in the coming years.
- Operational: Blockchain scalability remains an issue with public, permissionless blockchains. Consensus mechanisms create a tradeoff of throughput and trust.
- Operational: The blockchain validation process does not consider the trustworthiness of the original data at the initial input stage. Any decentralized identity platform must take special care that the input data is correct, usually authenticated by a issuing institution’s digital signature.
- Operational: Blockchains are vulnerable to 51% attacks. The decentralized nature of the system protects against this risk but does not completely prevent its occurrence.
Decentralized identity solutions are being investigated as a meaningful way to improve the identity infrastructure of the internet, and all actors that participate on it. While collaboration and opensource code is typical in the industry, there are a few private companies that are offering customized blockchain platforms for implementing private decentralized identity schemes.


















































