KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.


Unlock the power of industry-leading insights and expertise. Gain access to our extensive knowledge base, vibrant community, and tailored analyst sessions—all designed to keep you at the forefront of identity security.
Get instant access to our complete research library.
Access essential knowledge at your fingertips with KuppingerCole's extensive resources. From in-depth reports to concise one-pagers, leverage our complete security library to inform strategy and drive innovation.
Get instant access to our complete research library.
Gain access to comprehensive resources, personalized analyst consultations, and exclusive events – all designed to enhance your decision-making capabilities and industry connections.
Get instant access to our complete research library.
Gain a true partner to drive transformative initiatives. Access comprehensive resources, tailored expert guidance, and networking opportunities.
Get instant access to our complete research library.
Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
The cyber threat landscape that businesses, non-profits, and government agencies face today continues to evolve at an alarming pace, challenging cybersecurity staff and solutions to stay a step ahead of adversaries. As the realm of cyber threats expands, organizations have the difficult task of managing their attack surfaces effectively to protect their valuable assets. Attack surface management (ASM) has emerged as a crucial discipline that enables proactive cybersecurity strategies, mitigating risks by reducing an organization's exposure to potential attacks. CISOs are increasingly looking for portfolio consolidation opportunities, and ASM solutions provide the opportunity to centralize some functions that organizations are doing themselves as well as some functions that have been outsourced to service providers.
The attack surface is defined as the totality of all possible entry points within an organization, as well as the digital infrastructure of its subsidiaries and partners. It includes the hardware, software, storage, networks (on-premises and cloud), and identities (of users, service accounts, and devices) that attackers can exploit to deny service, gain unauthorized access, launch attacks, or compromise sensitive data. The attack surface is always changing, as the elements that compose it are themselves continually in flux, which means that round-the-clock monitoring and assessment is needed for due diligence.
ASM can play an important role in modern cybersecurity, enabling organizations to identify, analyze, and mitigate potential attack vectors effectively. As a discipline, ASM takes the attackers’ point of view. In fact, some vendors describe their ASM services as continuous red teaming. By gaining visibility into their attack surfaces as hackers perceive them, security teams can proactively defend against emerging threats, reduce vulnerabilities, and enhance incident response capabilities. IT security teams often lack an effective way to communicate risks about security vulnerabilities to business teams and IT asset owners. ASM solutions can enumerate vulnerabilities, analyze exposure, and combine business context and risk information in a way that is easier to consume and more actionable than previous methods.
ASM can enable deploying organizations to adopt a risk-based approach, allocating resources strategically to areas with the highest potential for compromise.
ASM solutions generally perform the following functions, and ideally in a continuous or frequent fashion:
To meet the challenges of the evolving threat landscape, ASM vendors offer innovative tools that address the following functional areas:
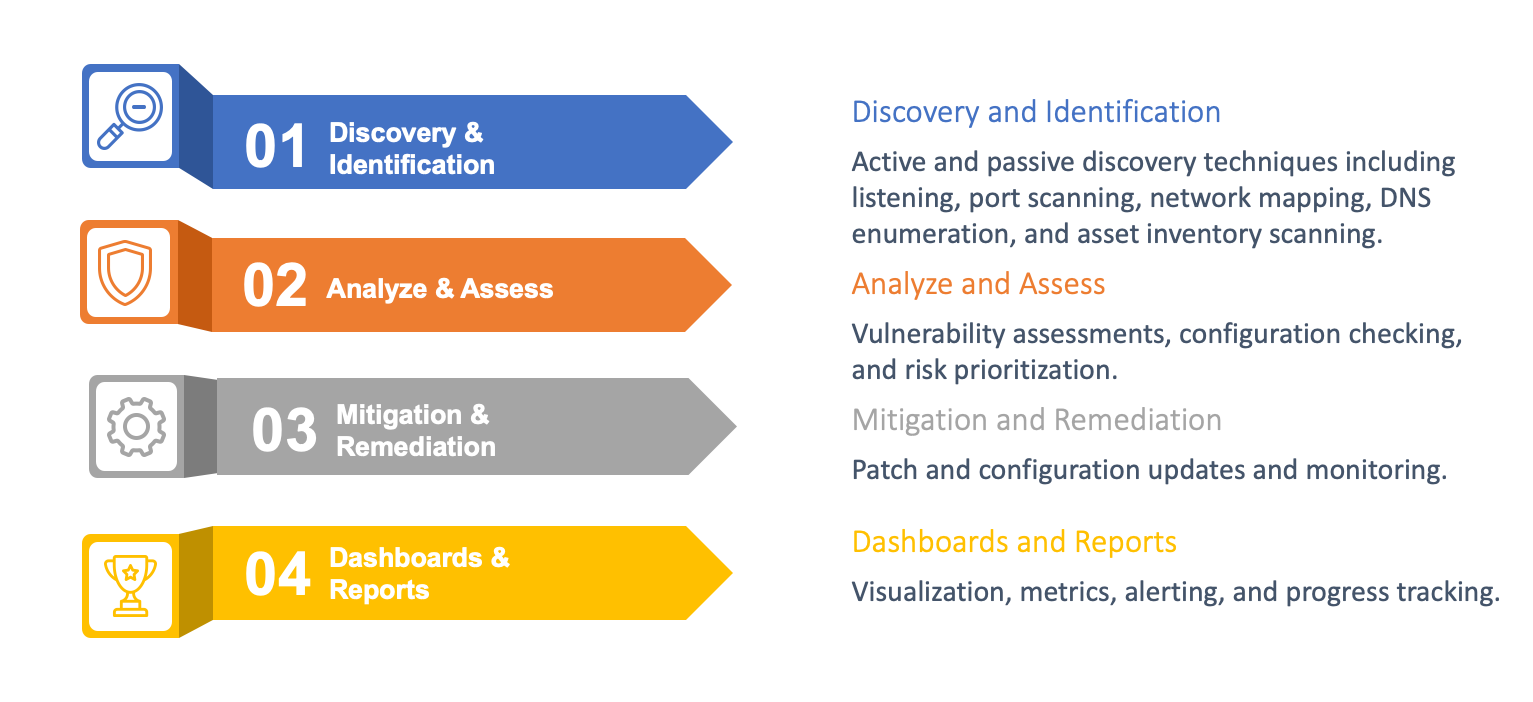
Figure 1: Key Functions of ASM
ASM can be a vital part in an overall enterprise risk management strategy. By effectively monitoring and reducing the attack surface, organizations can minimize their overall risk exposure and improve their resilience against cyberattacks. IT security teams may engage ASM services, but they are often not the owners of the systems that are found to need remediation. Thus, security teams must work with IT operations, development teams, business units, and executive management to ensure a comprehensive understanding of the attack surface and implement effective security measures.
ASM is an emerging and dynamic discipline. Here are some key areas of evolution in attack surface management:
Cloud (SaaS and IaaS): The widespread adoption of cloud computing has significantly expanded the attack surface. Almost every organization, large and small, makes use of SaaS applications today. Many enterprises use IaaS, and if not solely IaaS, then in hybrid mode with on-premises assets as well. Attack surface management must be able to discover, assess, and monitor resources hosted in these environments, as well as operate in and understand cloud-based architectural features such as elastic scaling, shared responsibility models, containerized applications, and shadow IT. All ASM solutions today are cloud-hosted, and the vendors are focused on external web and cloud threats.
Internet of Things (IoT): The proliferation of IoT devices and their various uses by enterprises increase risk and lead to new complexities in terms of attack surface management. Security teams and the tools they rely on must consider IoT vulnerabilities and the potential impact on the overall attack surface. This is an area of specialization that not all vendors address currently.
Dark Web Monitoring: Innovative ASM vendors have infiltrated dark web sites, ransomware-as-a-service sites, APT groups, instant messaging groups, discussion forums, and information exchanges. This enables them to find evidence of past successful attacks such as leaked information from data breaches, including companies’ proprietary information and individuals’ personally identifiable information (PII). ASM vendor researchers also may find compromised credentials, zero-day malware, insufficiently protected remotely controllable assets, and credit card and other account information for sale. Dark web monitoring can also give these ASM vendors advance notice of potential attacks and their targets, which they can then pass on to their customers.
Brand Protection: The features in ASM platforms for brand protection may include looking for signs of disinformation campaigns, social media reconnaissance, DNS manipulation, typosquatting, website spoofing, impersonation, and phishing. These functions are a subset of the broader category of brand protection, which also includes monitoring for improper or illegal use of logos, text, and media; social media manipulation; piracy, grey market sales, and counterfeit products; fake websites and fake or compromised mobile apps; etc.
DevSecOps Integration: Security must be integrated into the DevOps workflow. By incorporating security practices early in the development lifecycle, organizations can proactively address vulnerabilities and minimize the attack surface from the start. Many ASM vendors offer application security testing services in addition to their main solutions. Since most ASM vendors are focused on internet-facing assets, those particular solutions may not be suitable for applications intended for traditional intranet use.
Threat Modeling and Attack Simulation: Advanced threat modeling techniques and attack simulations provide valuable insights into potential attack vectors and their impact on the attack surface. These proactive approaches help organizations identify and remediate vulnerabilities before they can be exploited by adversaries. ASM solutions can aid in threat modeling exercises. The related field of breach and attack simulation (BAS) is still distinct from, and not generally a part of, most commercial ASM products and services today. We expect ASM and BAS to come together in more comprehensive offerings in future.
Regulatory Compliance: Most organizations are subject to one or more regulations, depending on the type of enterprise and the jurisdictions in which they operate. Privacy regulations such as the EU General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have garnered much attention in recent years. Other regulations in industries such as banking, finance, payments processing, insurance, healthcare, manufacturing, energy production, oil and gas, aerospace, etc., mandate specific security measures. Compliance requirements can directly and/or indirectly require organizations to have a clear understanding of their attack surface and implement measures to protect sensitive data governed by pertinent regulations. Some of the solutions analyzed in this report have compliance modules that are designed to help customers measure and report on compliance with specific regulations or frameworks.
This KuppingerCole Leadership Compass provides an overview of vendors and their product or service offerings in the ASM market.
Highlights
The Attack Surface Management market has emerged in the past few years with antecedents in asset management, vulnerability management, penetration testing, red teaming, cyber test ranges, and, to a lesser degree, BAS. ASM combines many of these techniques, and in many cases automates these techniques, to deliver a more frequent and cost-effective set of related security capabilities. Vendor solutions in the ASM market are maturing. There is a wide array of possible features available in the products and services in the market today. At present, most vendor solutions are focused on external ASM, or EASM: what can be tested and assessed from outside customer organizations’ infrastructure. A broader view of ASM is reflected in the market definition for this research in which ASM solutions are defined as those designed to address cyber threats stemming from organizations’ ever-growing attack surface. The overall attack surface for organizations is made up of two distinct parts:
Digital Attack Surface: operating systems, applications, websites, APIs, virtual machines (VMs), containers, cloud-hosted services, code, shadow IT, etc.
Physical Attack Surface: workstations, laptops, servers, mobile phones, hard and USB drives, IoT devices, operational technology (OT) and industrial control systems (ICS) components, etc.
We believe that the ASM market will move toward this more complete definition, including covering internal and physical assets like the CAASM market. This would require the availability of on-premises components, such as appliances (physical or virtual) or installable agents for endpoints. The EASM and CAASM functionality split is not likely to be tolerated by enterprise buyers of ASM products and services indefinitely.
The ASM market today is already quite large and diverse, with both large and small, and established and startup vendors present. We expect this market to continue to evolve, mature, and grow.
ASM, therefore, can benefit many types of organizations, but given that feature sets in current examined offerings are primarily aimed at external ASM, those with extensive web estates and customer-facing infrastructure will see the most value. Each solution evaluated has different strengths that will appeal to different organizations, depending on their particular requirements.