KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.


Unlock the power of industry-leading insights and expertise. Gain access to our extensive knowledge base, vibrant community, and tailored analyst sessions—all designed to keep you at the forefront of identity security.
Get instant access to our complete research library.
Access essential knowledge at your fingertips with KuppingerCole's extensive resources. From in-depth reports to concise one-pagers, leverage our complete security library to inform strategy and drive innovation.
Get instant access to our complete research library.
Gain access to comprehensive resources, personalized analyst consultations, and exclusive events – all designed to enhance your decision-making capabilities and industry connections.
Get instant access to our complete research library.
Gain a true partner to drive transformative initiatives. Access comprehensive resources, tailored expert guidance, and networking opportunities.
Get instant access to our complete research library.
Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
The landscape of enterprise and personal computing technology is continuously evolving. It does not seem that long ago that the work environment consisted of desktop computers and landline phones. Traditional management of desktop computers at the time relied on manual software updates and patches layered on top of each other. Later, “Gold Images” of desktop operating systems were used to provide a good, known state of the operating system (OS) but still required patches on a routine schedule, which would become what was known as traditional endpoint management.
As mobile phones became economically available, laptops and tablet computers replaced many stationary desktop computers; the business could control the employee device regarding its OS, the software applications used, and the security controls when the device was within the organization's perimeter. Client management tools were used to manage these environments. Client management involves capabilities such as OS deployment, software distribution, patch management, monitoring, and remote-control tools to support administration or to help automate other support functions that are typically executed manually.
Later, organizations needed to quickly deal with the introduction of the bring-your-own-device (BYOD) paradigm shift. Organizations required policies that defined the boundaries of BYOD, including the ability to segregate business data and applications from personal data and applications. Mobile device management (MDM) provides the tools to control the device functionality and help manage the lifecycle of these mobile devices and their platforms. Enterprise Mobility Management (EMM) solutions added mobile information, as well as application and content management. The ability to push software, updates, or patches to devices has become what is known as modern endpoint management.
Since then, work environments have continued to change. The range of endpoint device types has expanded past desktops, laptops, tablets, and mobile phones. Now endpoint types include printers, IoT devices, wearables like Apple Watch, and, more recently, endpoint devices that support virtual/augmented/mixed reality environments using headsets such as Oculus and HoloLens. Businesses seek to improve productivity and efficiency, while employees want to work-from-anywhere (WFA) at any time. And as we've seen with the Covid-19 world today, the ability to work from home is still imperative, requiring endpoint devices to access enterprise applications and data as if they were in the office. Given the WFA workforce paradigm, employees' experience interacting with their virtual workplace that utilizes endpoint applications, software, and other online tools must also be considered and supported.
With the complexity and growing number of technologies involved in linking employees to corporate data on-premises and in the cloud, mobile device management has undergone several iterations and approaches. Many enterprises are now standardizing on a Unified Endpoint Management (UEM) approach.
This KuppingerCole Leadership Compass provides an updated overview of vendors and their product or service offerings in the UEM market, ranging from vendors within more localized geographic regions to vendors with a global presence. The report also considers these services in the context of the hybrid, on-premises, and cloud, with IT service delivery models commonly found now in enterprise environments.
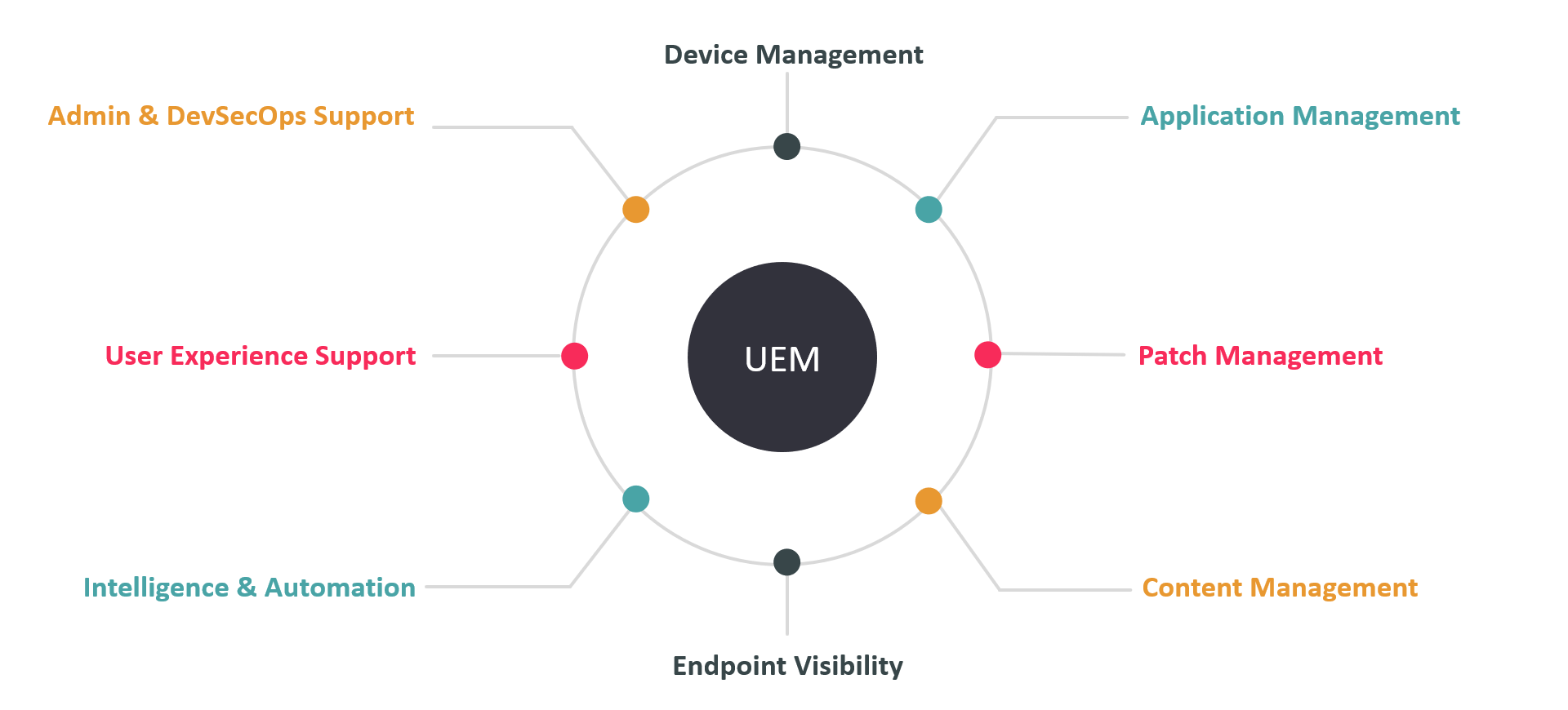
Figure 1: Unified Endpoint Management