1 Introduction
Achieving security compliance for IT architecture is critical to ongoing data security and privacy and protect organizations from cyberattacks. It refers to the adherence of established standards, regulations, and best practices that can be a part of internal policies or part of legally binding international legislation and recognized security frameworks. In practice there must be a means to implement controls, policies, and procedures designed to safeguard sensitive information, prevent unauthorized access, and mitigate security risks. Control methods can be manually configured via bespoke internal systems or via off-the-shelf software solutions designed to integrate with IT infrastructure.
Managing IT security compliance has long been a challenge but modern IT architectures with IaaS, SaaS, remote working, third party access to networks and many thousands of identities to manage, has made the task harder. The use of multiple cloud services often involves shared responsibility for security and compliance, not always well regulated internally. This can lead to confusion, security weaknesses and compliance failures if production systems are not subject to correct compliance standards and updated accordingly in line with changes in operations or policies. In fact, changes in operations or architecture should lead to policy changes in a well-regulated business. Organizations are therefore looking for highly granular, highly capable but easy to deploy solutions to maintain security compliance in the most dynamic way possible.
Everything in the IT estate must be compliant [with regulatory standards]. This includes cybersecurity tools such as firewalls, web and mail filtering, Data Leak Protection (DLP) and Identity and Access Management (IAM) platforms etc. All are designed to prevent and detect attacks on data, but they must be applied correctly to ensure that compliance is achieved. In other words, they must be seen to not just to work but to a technical and legal framework that may be further refined by business policies.
Information technology during the last few years has converged with engineering innovations to create a whole new digital world. This has led to a large stack of technologies. In fact, the large number of versions for each such technology has further increased the complexities. There are three broad challenges from a security & compliance perspective:
- Maintaining Confidentiality, Integrity and Availability is now a complex subject but a necessity
- Continuous defense (hardening) against sophisticated cyberthreats
-
Continuous assessment vis-a-vis regulatory compliance standards like PCI DSS, ISO 27001, SOX, HIPAA, NIST 800-53, 20 CSC, COBIT and technical controls such as CIS benchmarks and their remediations (if required)
Organizations that fail to meet certain international standards such as the above may face heavy financial penalties. Also, many government, defense, health, or pharma customers will demand compliance with technical security standards such as ISO 27001 or NIST as a prerequisite for doing any business with suppliers. Companies working in the financial sector are subject to a myriad number of regulations affecting fraud prevention, security, and data protection.
Other aspects of security compliance involve implementing strict access controls to ensure that only authorized individuals can access sensitive data and systems. This might involve role-based access control (RBAC), multi-factor authentication (MFA), and least privilege principles being applied and checked for efficacy.
Regularly assessing and addressing vulnerabilities in IT systems is crucial. This involves conducting vulnerability assessments, patching software, and maintaining up-to-date security measures such as regular and often risk scoring of events and workflows. This process is aided greatly by having a central reporting dashboard or window that gives up to date aspects of IT security compliance.
It is important to recognize that compliance with standards and frameworks should go beyond a minimal collection of reporting obligations. A business led approach to compliance not only ensures transparent compliance processes but also looks at addressing a particular business need that an organization might have.
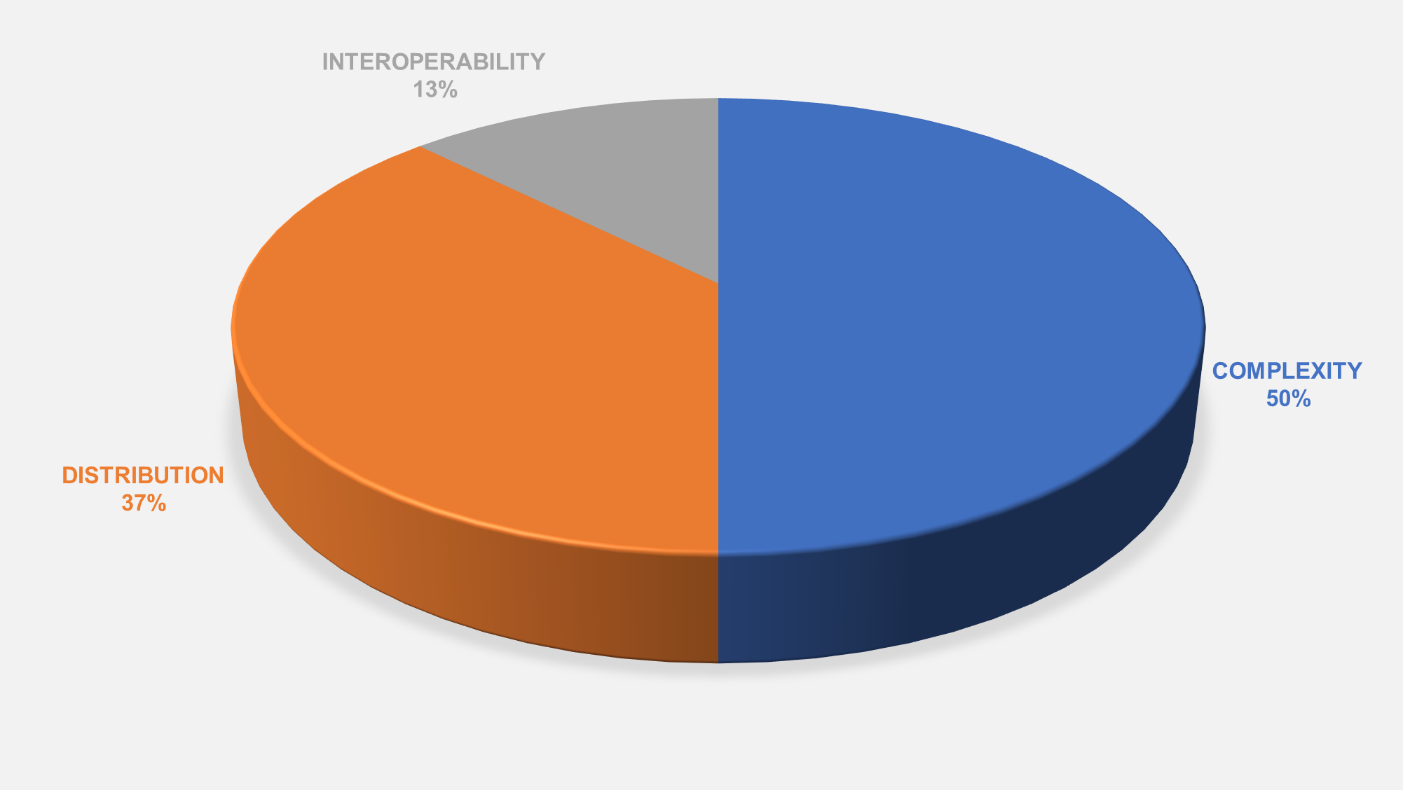
Figure 1 The most challenging aspects of protecting information according to a survey of KuppingerCole clients. (Source: KuppingerCole Analysts)
A well-defined incident response plan helps organizations respond effectively to any security incidents. The plan outlines steps to take when a breach occurs, minimizing potential damage and ensuring a swift recovery.
All aspects of security compliance will be greatly assisted by an IT security compliance platform or software application that can automate much of the security audit checks and risk scoring. Given the complexity of modern organizations and the time and budgetary constraints, such a platform is now almost essential to the ongoing security and viability of any business.
We advise buyers and IT chiefs to look at the market and decide which platform has the capabilities and features needed for their type of business and the networks in their wider orbit, third parties and supply chain. More than anything, the ability to reliably automate as much of the compliance checking and remediation processes should be at the top of buyer’s minds.


















































