1 Introduction
Digital identity is a critical business-enabling technology for every business. However, as is borne out by cybercrime reports year after year, digital identity is also a primary vector through which businesses are attacked. Many businesses still lack an IAM (Identity and Access Management) that is adequate to meet the various requirements, from efficient processes for granting and revoking access entitlements to fulfilling regulatory compliance requirements and mitigating cyber risks.
The risks of not having well-maintained and secure IAM solutions within organizations are great, ranging from lower productivity associated with password resets and incorrect entitlements; loss of data such as employee and customer PII; loss of trade secrets and other valuable business information; diminished revenue from reputation damage and fraud; to unwittingly becoming a vector of attack to other members in a supply chain.
Identity & Access Management has come a long way since the inception of Directory Services, and it is still actively evolving. KuppingerCole’s view of IAM over time begins with an IAM in whose primary purpose was to prevent unauthorized access to secure resource. With its focus on access administration, the IAM core technology started to include Identity Provisioning as well as the core capabilities to authenticate, authorize and audit.
A further generation of IAM not only tried to prevent unauthorized access to a resource, but it also added the capability to detect it. Access Governance was included as a core technology for IAM with a focus on administration with business participation, and the ability to detect was partially due to integrations with Security Information and Event Management (SIEM) products making its way onto the stage.
In this latest iteration, IAM adds to its ability to prevent and detect by also providing the ability to respond to the security threats. New IAM technologies included Access Analytics and Intelligence. As the landscape of information security threats changes, so do the IAM capability requirements.
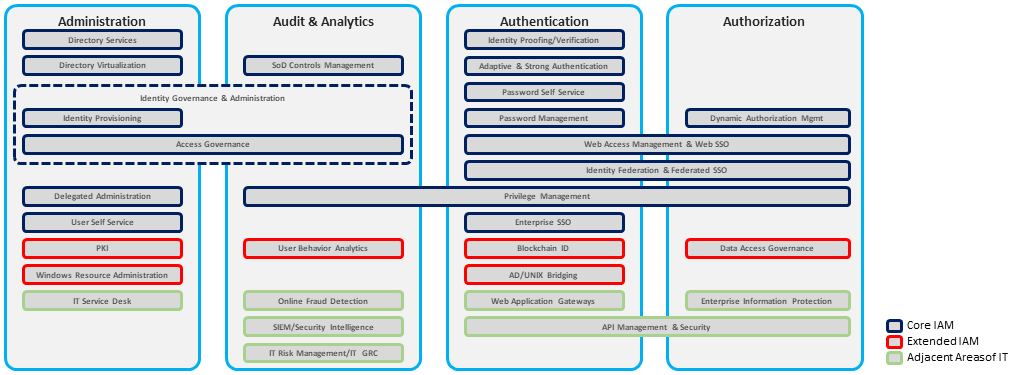
While there are many elements within IAM, there are some key areas:
Identity Administration: The ability to administer identity lifecycle events including provisioning/de-provisioning of user accounts, maintaining identity repositories, managing access entitlements, and synchronization of user attributes. A self-service user interface allows for requesting access, profile management, password reset, and synchronization. Configurable cloud-native connectors offer automated user provisioning to both on-premises as well as SaaS applications. Other common identity administration capabilities include administrative web interface, batch import interface, delegated administration, SPML, and SCIM support.
Access Management: This category includes authentication, authorization, single sign-on and identity federation for both on-premises and SaaS applications delivered as a cloud service. The underlying support for industry standards such as SAML, OAuth, and OpenID Connect can vary but are largely present in most IDaaS offerings. API security and web access management gateways are fast becoming a differentiator for IDaaS vendors looking to offer competitive access management capabilities and so is social identity integration – which now represents a basic qualifier for consumer access use-cases.
Access Governance, Analytics, and Intelligence: This group of capabilities that are often absent from the portfolio of most IDaaS vendors, partly due to architectural limitations and partly due to ownership issues. While many organizations still prefer to keep access governance on-premises for better control and auditing purposes, others are moving it to the cloud for ease of integration and better time-to-value as their SaaS portfolio continues to grow.
Factually, while business need a set of IAM capabilities, some of these are of specific relevance. One of these is Access Governance, which is essential to meet regulatory compliance requirements. Access Governance is one of the core building blocks of IAM, and it frequently comes as part of comprehensive IGA solutions, but is also available as focused solution. The latter potentially allow for a rapid deployment.
Kleverware, a French software vendor, provides such a focused Access Governance solution that can be used stand-alone, in combination with existing IGA and Identity Provisioning solutions, or in combination with ITSM tools such as ServiceNow.


















































