1 Introduction
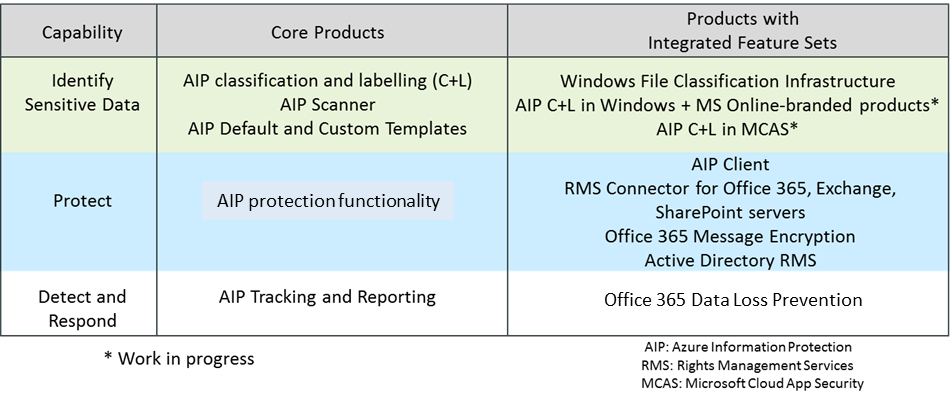
Azure Information Protection (AIP) provides data protection with Classification, Labeling, and Protection capabilities. It is a core component of data protection across the Microsoft 365 suite (Office, Windows, Azure) and 3rd parties as well. Sometimes, you’ll hear the term Microsoft Information Protection to define these capabilities.
Clients’ data protection challenges span multiple technologies, including data leakage prevention (DLP), encryption, access control, digital rights management (DRM), and security monitoring. As illustrated in Figure 1, Microsoft has taken an integrated approach to data protection in Azure and other product lines.
Enterprises attempting to deploy data protection technologies through DLP, DRM, or other projects face significant limitations and challenges. DLP and DRM frequently fail due to a lack of clear focus, failure to get critical business unit support, and difficulties of integrating supporting technologies. KuppingerCole recommends clients form realistic expectations of what can be achieved with DLP and DRM, and prioritize business unit engagement.
Here is the real benefit: Successful data protection can reduce the frequency, quantity, and consequence of accidental information leakage and policy-violating user behavior. It cannot always stop sophisticated hackers and determined insider threats. It cannot bring the risk of leakage to zero. The good news is that even just reducing accidental leakage and policy-violating behavior significantly lowers organizations’ massive and growing information risk. Clients should set the bar for expectations there.
Microsoft’s data protection solutions are subject to the same operational limitations of DLP and DRM – difficulty of covering all leakage vectors, thwarting sophisticated adversaries, getting user buy-in – as other products. However, because Microsoft addresses the user experience with comprehensive data classification, labeling, and tracking features its solutions show considerable promise for protecting Office documents and other unstructured data files that may contain a large portion of the enterprise’s confidential information. The Microsoft Cloud Application Security (MCAS) solution – acquired from Adallom in 2015 – is highly complementary to AIP. Like other cloud access security brokers (CASBs), MCAS can discover and control unapproved data flows, aka “shadow IT.”
KuppingerCole recommends clients invested in Office 365 and Azure consider adopting AIP and other Microsoft data protection solutions for Office documents and emails. However, most clients should also consider third-party enterprise DLP solutions, or channel-specific DLP solutions, to cover most non-Microsoft document or data types and leakage vectors. Clients should also be aware that Microsoft’s data classification and labeling infrastructure and formats are becoming widespread in the market and ensure that 3rd party DLP solutions are well integrated with them.


















































