KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.


Unlock the power of industry-leading insights and expertise. Gain access to our extensive knowledge base, vibrant community, and tailored analyst sessions—all designed to keep you at the forefront of identity security.
Get instant access to our complete research library.
Access essential knowledge at your fingertips with KuppingerCole's extensive resources. From in-depth reports to concise one-pagers, leverage our complete security library to inform strategy and drive innovation.
Get instant access to our complete research library.
Gain access to comprehensive resources, personalized analyst consultations, and exclusive events – all designed to enhance your decision-making capabilities and industry connections.
Get instant access to our complete research library.
Gain a true partner to drive transformative initiatives. Access comprehensive resources, tailored expert guidance, and networking opportunities.
Get instant access to our complete research library.
Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
With the rapid expansion of IT environments and adoption of cloud, and the ongoing Digital Transformation, the need to provide secure access to organizational resources has become paramount. The number and types of security tools addressing ever-evolving threats that are in use across a typical organization continues to increase. Managing network connectivity and security has become more expensive, complex, and time-consuming.
Secure Access Service Edge (SASE) solutions are designed to consolidate network and security components, simplify management and licensing, and improve usability. SASE is the union of a number of different networking and security technologies designed to improve security posture as well as connectivity for remote offices, cloud services, contractors, and remote employees, while driving down the cost of connectivity.
KuppingerCole defines SASE as the bundling of:
Therefore, we see that SASE is not a brand-new technology but is instead an innovative packaging of security and networking solutions that can be better positioned to solve contemporary and evolving business requirements. The technologies involved encompass endpoints and both on-premises and cloud resident infrastructure and applications. SASE Integration Suites must be capable of supporting hybrid environments. Moreover, most organizations operate in and are further pursuing multi-cloud architectures.
Secure Access implies strong, multi-factor authentication and authorization for remote users and devices, threat detection and protection, and fine-grained access controls. Work From Home (WFH) and other drivers for remote work have been supported by VPNs for more than two decades. The Covid pandemic necessitated WFH en masse, and the technologies that remote work relies upon have proven to be highly effective. However, in many cases, the performance of traditional VPNs has been strained. Scalability has been insufficient. Managing network segmentation in conjunction with VPN access has become exceedingly difficult in large enterprises. Organizations that allowed username/password authentication to VPNs have become more aware of the significant risks of weak authentication and have moved to require MFA. The deployment of MFA has increased complexity, thereby making VPNs more difficult to manage.
Many organizations accept that Work from Anywhere (WFA) will be the norm going forward. The need for Secure Access is greater than ever, with fraud, ransomware, and corporate espionage on the rise. Remote worker access, including employees and contractors, needs to be properly secured with strong authentication services and granular access controls. Moreover, assurances that end user devices are not compromised must be part of the Secure Access equation. Remote workers and contractors now do much of their work in the cloud as well as by accessing resources in corporate data centers.
Prior to the pandemic, many kinds of organizations were experiencing tectonic shifts in application and user distributions. The move to the cloud for applications and storage had been gaining pace for the previous decade. Covid accelerated the migration to cloud services. Protecting sensitive resources of an increasingly distributed enterprise with a large mobile workforce is becoming a challenge that siloed security tools are not able to address effectively. In addition to the growing number of potential threat vectors, the very scope of corporate cybersecurity has grown immensely in recent years. SASE was postulated as a means to connect distributed users more efficiently and securely with distributed applications.
Organizations with a focus on IT security have been making users authenticate strongly for years and have brought remote worker and branch office traffic back to the enterprise data center(s) for security analysis. However, organizations with legacy VPN architectures found that remote workers, offices, and contractors sometimes exercised options that decreased overall security when encountering underperforming, backhauled connections. Some chose to implement split-tunneling, allowing direct-to-cloud access for SaaS while routing internal application traffic to data centers. In other cases, users disconnected themselves from slow VPNs in order to go cloud-direct. In both of those scenarios, enterprises may lose the ability to apply network, application, and data security policies. Older style, isolated VPN technology will likely be replaced by contemporary, integrated SASE VPN solutions in the medium term. Another problem that SASE’s updated approach to VPN addresses is automated routing and failover between nodes. Early generation VPNs required user intervention to switch between servers, which could often result in poor network performance as perceived by the user. Moreover, advancements in cryptography and tunneling protocols such as WireGuard as realized in some SASE solutions will provide security and routing benefits.
The Secure Service Edge part of SASE refers to the need for security where users and networks intersect. Examples include LAN to LAN, data center to data center, branch office to corporate, franchises to headquarters, remote production centers to HQ, sensors to municipalities, on-premises to cloud, and remote users connecting to all scenarios above. Security for these use cases tends to be more focused on device level assurance of integrity, authentication, and authorization, supported by policies based on certificate authentication, challenge-response, and allow- and deny-lists. In this scenario, NGFWs or FWaaS can provide network and transport layer security, and CASB and SWG solutions provide the session and application layer access controls and data object security. RBI acts as an application layer web proxy that mediates users’ web requests, sandboxes suspicious content, and renders web and application content safely, transmitting a view of the content back to the user rather than the content itself.
SD-WAN technology was developed to enable businesses to use readily available high speed internet connections rather than point-to-point private network services such as T1 lines, Frame Relay systems, or Multi-Protocol Labeling Switches (MPLS), or VPN mesh architectures such as Dynamic MultiPoint VPN (DMVPN). Private networking solutions have been reliable and reasonably secure for most customers, but expensive. These private networking solutions are mainly delivered by telcos. In many cities around the world, it is now possible for organizations to provision high speed internet connections (between 100 Mbps to 1+ Gbps) from not only telcos, but also cable providers and other internet service providers, often at a significant discount compared to point-to-point solutions. Mobile Network Operators (MNOs) offer high-speed 4G LTE and 5G across many regions as well. SD-WAN has also improved network and application performance by getting remote users and remote offices closer to SaaS applications and enterprise services implemented at the edge (services and entry points installed in high-bandwidth co-location facilities or by Content Delivery Networks [CDNs]).
SD-WAN, SASE, and CDNs vendors use a variety of techniques to “accelerate” TCP connections from the perspective of end users. Many point-to-point connections, including those from remote workers, have unused capacity. The design of the transport protocol itself can be the source of those kinds of bottlenecks. TCP, as implemented in OSes, will ramp up the volume of data transmission until clients begin experiencing latency, packet loss, jitter, etc. Then networking drivers and OSes will cut the data volumes (window size) in half, and start trying to increase it again, but linearly.
A leading TCP optimization method involves the use of transparent TCP proxies. TCP proxies sit between clients and target resources and buffer 2-3 TCP sequences ahead per connection. This enables clients to receive data faster, and in the event of packet loss, retries go to the proxy, which is in between and has stored up the next few rounds of data to transfer. This method decreases the time that end users typically experience for large downloads, uploads, and streaming. TCP optimization is particularly useful at the “edge,” at Points of Presence that may be physically far from data centers and cloud resources.
Other TCP optimization methods involve changes to TCP flows, including Selective ACKs to mitigate duplicate transmissions, using larger initial window sizes, and Bottleneck Bandwidth testing to determine the optimal rates per connection.
The drawback for SD-WAN is that there is no explicit security beyond transport layer encryption: meaning that point-to-point connection authentication and access controls, user session authentication and authorization, and application authentication and access controls are not addressed.
Since SD-WAN emerged, a number of security tool types have been extended to cover shortcomings in the underlying model. SWGs are proxies used to consolidate and control user and app web utilization. Endpoint Security tools discover and prevent exploitation of vulnerabilities and execution of malware, provide application controls, and URL/content filtering. NGFWs are application- and (in some cases) identity-aware firewalls. FWaaS are cloud-hosted NGFWs. CASBs enable shadow IT discovery, Network Access Control (NAC) points, and Data Leakage Prevention (DLP) Policy Enforcement Points (PEPs) for cloud-hosted resources. Security stack vendors began packaging these as solutions to help customers deal with the increasing complexity and risks of SD-WAN.
Zero Trust has arisen over the past decade and has become a primary means of addressing access control use cases. Given the focus on the networking aspect, it is usually abbreviated as ZTNA (Zero Trust Network Access). Often expressed as "Never trust, always verify", ZTNA is an embodiment of the principle of least privilege, and at its core mandates that every access request be properly authenticated and authorized. Thus, IAM (Identity and Access Management) is a foundational element for ZTNA. Proper access management in service of ZTNA means considering the requesting user's attributes, authentication and environmental context, permissions and roles, source device information, and the requested resource attributes. Zero Trust Architecture implies a concept where clients can access services from everywhere, not relying only on internal network security mechanisms. In fact, ZTNA has become the strategic IT security paradigm for many services and products. Therefore, ZTNA is well-suited to help mitigate the shortcomings of SD-WAN and provide the security structure for SASE.
SASE Integration Suites bring the power, flexibility, and costs saving potential of SD-WAN together with security posture enhancements afforded by integrating CASB, Endpoint Security, DLP, NGFW, SWG, RBI, and IAM in a Zero Trust Architecture. SASE, like Zero Trust itself, embodies a wide range of functions that are often instantiated in multiple products. Most enterprises, government agencies, non-profits, and small businesses already have a plethora of security and networking solutions in place. SASE Integration Suites offer the advantage of centralizing administrative control over these disparate technologies. SASE Integration Suites must interoperate with tools in each security and identity domain to provide comprehensive coverage and management for all requisite functions.
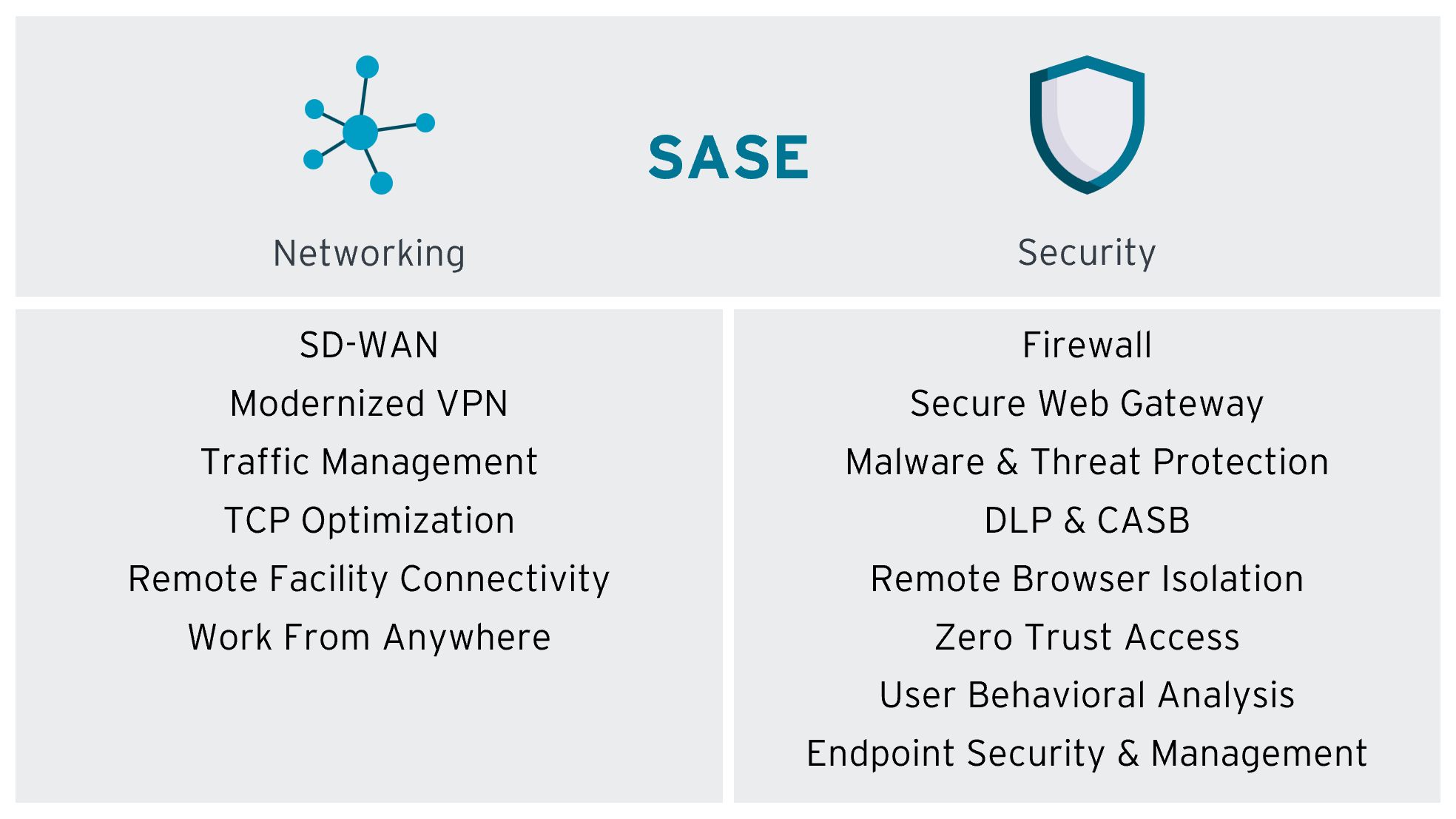
Figure 1: Overview of SASE Functions