1 Introduction / Executive Summary
Cyber-attacks are on the rise as we all know from the seemingly constant breaking news stories. Government agencies large and small are under attack. Businesses and non-profit organizations are under attack. Small to medium sized business (SMBs) that at one time felt as if they had no major cybersecurity worries find themselves increasingly targeted by cyber criminals and fraudsters. Ransomware attacks continue to accelerate, abetted by the cyber insurance industry. Ransom demands are jumping. To combat modern cyber threats, organizations have been investing in more and more tools focused on threat detection leveraging big data analytics and user behavior modeling―generating massive waves of alerts, which too often turn out to be false positives.
Analysts spend too much time chasing benign behavior and consequently, real attacks are slipping through. Behavioral detection solutions powered by machine learning offer better efficiency, yet they are probabilistic in nature, requiring cycles of manual effort to truly track down and confirm if a threat is present. Facing these challenges, further complicated by the growing shortage of skilled security analysts, many organizations started looking for alternative approaches for detecting and responding to threats in real time.
One of the oldest of such alternatives, predating modern IT by at least a couple decades, is using honeypots to lure attackers with strategically placed fake computing resources. Like police sting operations, this involves deploying carefully crafted traps within and/or adjacent to the corporate computing environment, which appear to be a legitimate part of the IT infrastructure and seemingly contain information valuable for hackers. However, these fake resources are distinct from the real assets and are closely monitored; since there is no reason for legitimate users to use them, any access attempt can be considered a reliable sign of an ongoing attack.
This deterministic nature of honeypots has made them a useful tool for both academic researchers and security experts. Unfortunately, such solutions have been difficult and costly to deploy at scale, unless deployed as part of distributed deception platform; they also generate lots of security telemetry which requires expertise to analyze properly. And yet, as the continuing de-perimeterization of enterprise networks makes traditional security tools like packet filter firewalls or signature-based antivirus less and less relevant, the interest in deception as a methodology and as an integral part of the overall cybersecurity architecture is growing.
Distributed Deception Platforms are systems that are designed to simulate a variety of computing assets and environments for the purposes of drawing in would-be attackers to clearly alert IT security teams to the presence of attackers, drawing attackers away from real assets, and allowing IT security teams to study the TTPs of attackers in order to better defend against current and future attacks.
DDPs are the logical evolution of honeypots and have been productized for easier commercial deployment and use. DDPs can work well in conjunction with Network Detection & Response (NDR) and Endpoint Detection and Response (EDR) tools for enterprises with high security needs. One of the advantages of DPPs is that when activity is detected within a properly deployed system, it is almost guaranteed to be malicious. This makes detection of malicious activity comparatively easy. On the other hand, Endpoint Detection & Response (EDR) and NDR tools work by analyzing many endpoint events and network traffic, applying machine learning (ML) detection models to probabilistically discover outliers and identify potentially malicious events. DDP solutions have progressed toward common features sets, architectural patterns, and topographies. DDPs are becoming easier to afford, deploy, and manage for both SMBs and enterprises.
EDR solutions operate in areas where software agents can be installed on devices. This can provide coverage for typical office environments, but is not effective in places where agents cannot be installed, such as ATMs, IoT devices, Industrial Control Systems (ICS), medical devices, etc. In these settings, NDR solutions can offer visibility and controls, and DDPs can be an active defensive measure on the frontline with decoys that emulate these devices and through IAM protection (most commonly Active Directory).
The network security industry is moving in the direction of "XDR", sometimes standing for eXtended Detection & Response, which is a union of EDR and NDR. DDPs can be considered an advanced element of XDR solutions, as they aid IT security teams in discovering anomalous and malicious behavior at various layers across the infrastructure.
Deception technology is also a constituent of the KuppingerCole Information Protection Life Cycle (IPLC). The IPLC and Framework describes the phases, methods, and controls associated with the protection of information. The IPLC documents three stages in the life of information and multiple categories of controls which can be applied to secure information. The "main sequence" of information is Active Use Life. Active Use Life is a concept borrowed from the field of archaeology, defined as the period when a human made artifact is actively in use. Information is a human construct, with a beginning and often an end, thus the definition works well for the IPLC. Deception technologies fit into the Active Use Life phase of the IPLC.
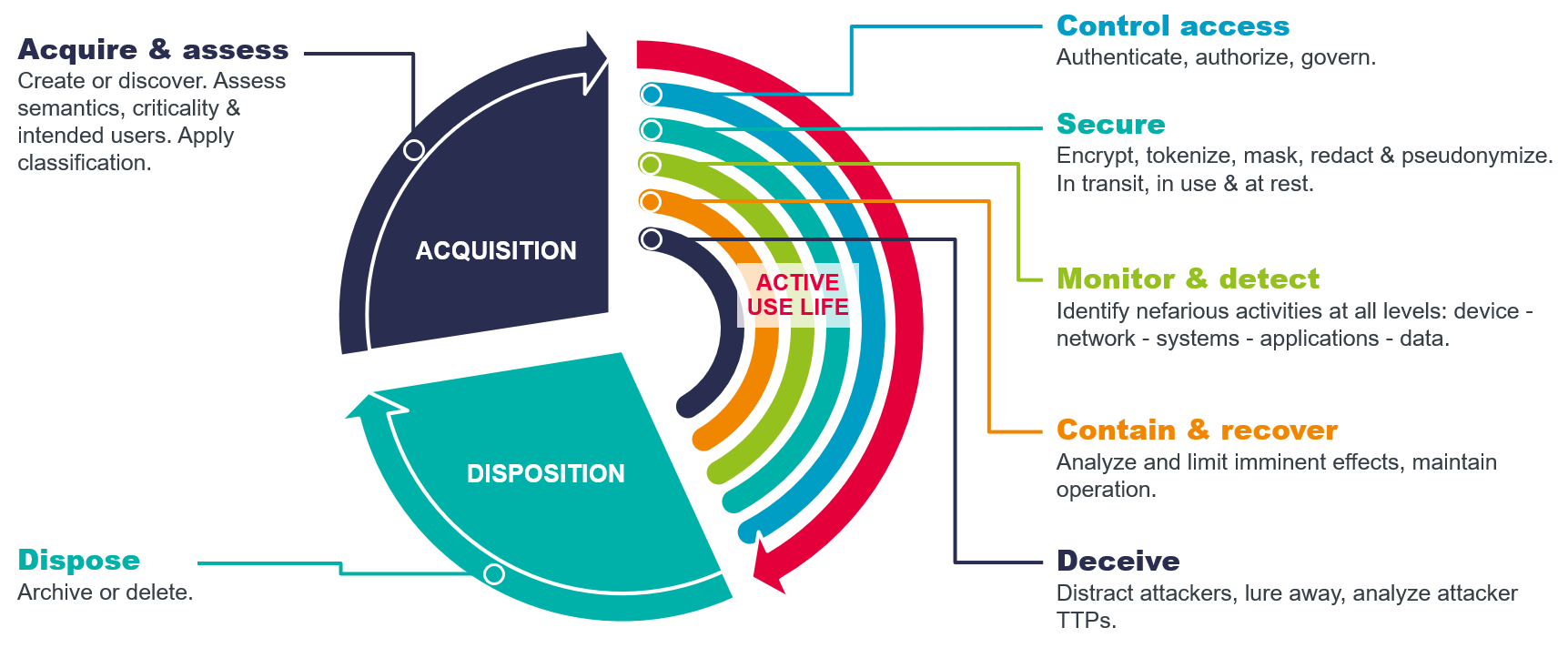
At a high level, DDPs are composed of traps, lures, misdirection, and management systems. Some vendors use the term "decoys" synonymously with traps. Others call lures "breadcrumbs", "baits", or "honey tokens". Given that digital identity is a primary vector in attacks, DDP vendors provide deception assets for IAM, which are specific combinations of traps and/or lures. Identity Detection and Response solutions add the ability to show potential attack paths, and they can hide legitimate credentials and Active Directory objects, which prevents credential theft and privilege escalation. Attackers can also be identified when they conduct unauthorized queries against identity data stores. Disinformation can be provided as a response to those unauthorized queries, which will redirect the attacker to a decoy for the monitoring and analyzing their TTPs.
-
Traps: servers, virtual servers, or appliances that host simulated assets for the DDP. Trap servers can be Windows servers or desktops, Linux machines, Macs, cloud instances or containers (in either public or private clouds), VPNs, industrial control servers, sensors, meters, specialized manufacturing and medical equipment, etc. In cloud computing environments, traps can be access keys, storage buckets, serverless functions, databases, and containers. Trap servers should run applications that are typical in the reference or production environment, such as web servers, mail servers, content management systems, collaboration services, file shares, financial applications, remote desktop "jump boxes", industrial control applications, IoT device management applications, etc. Application and service simulation detail can vary between vendor solutions, and devices or applications simulated; the range of simulation runs from listening on standard ports, session establishment, full protocol responses, and customizable interactions.
-
Lures: objects that are designed to appear interesting to attackers in order to get them to interact with the full DDP. Lures can take many forms, examples of which are listed below. Lures can be hosted in many locations, depending on customer preferences.
- Services
- Files
- Credentials
- x.509 certificates
- SSH application configurations and keys
- Scripts
- RDP sessions
- Database content
- DNS entries
- Beacons
- Cookies
- Shortcuts
- Network shares
Lures should be placed on endpoints and servers within customer organizations as well as in SaaS apps where appropriate.
-
IAM deception: given that credential takeover and escalation are critical vectors in most cyber-attacks, DDPs offer a variety of techniques for creating and managing fake IAM infrastructure and credentials. Most vendor solutions support to differing degrees the deployment and management of Microsoft Active Directory (AD) components, credentials, and objects. Some DDPs deploy parallel AD components with trusts back to the customers' production AD domains. Other DDPs create fake accounts and other objects in customer production AD infrastructure. A few vendors interoperate with generic LDAP and IDaaS. In order to make sure that attackers do not bypass fake credentials and use real credentials, full IAM and AD monitoring and PAM should be in place.
-
Management consoles: interfaces for customer and/or MSSP administrators to deploy, configure, manage, and monitor traps and lures. DDP solutions often have facilities that perform automated analysis of customer assets to suggest and create traps and lures that appear realistic to attackers. These interfaces also allow customers or their MSSP delegates to modify configurations as needed, monitor activities within the deception environment, and conduct investigations on in-progress attacks. Management consoles can be deployed on-premises, in public or private IaaS, in the vendor's cloud, or at MSSPs.
Management components should adhere to pertinent standards and offer API integration. DDPs need to be able to interoperate with other parts of the security architecture, especially SIEM and ITSM systems.
1.1 Highlights
Top Ten Findings in the Leadership Compass on Distributed Deception Platforms:
- Deception is an established and growing specialty in cybersecurity. Years ago, enterprises outside of cybersecurity may have considered deploying and running honeypots to be exotic and not cost effective, but modern vendor implementations and managed services bring these capabilities within reach and affordability of many kinds of organizations.
- DDPs can be thought of as extensions of detection technologies.
- By design, DDPs have a far lower false positive rate than IDS/IPS, SIEMs, and some other tools, which can improve efficiency in SOCs. This is not to say that other detection tools and security data repositories are obsolete; rather, DDPs can be good adjuncts to the standard security suites.
- DDPs will become core parts of XDR platforms in 3-5 years.
- Properly deployed and maintained DDPs deliver highly specific and actionable cyber threat intelligence.
- Traps and lures are foundational components of DDPs, but identity deception is essential because attacks leverage user and admin credentials.
- OT and ICS environments often lack security tool instrumentation, leaving NDR and DDP technologies as the few means for detecting attacks within.
- The Product Leaders in Distributed Deception Platforms are, in alphabetical order, Acalvio, Attivo Networks, CounterCraft, and Zscaler.
- The Innovation Leaders in DDP are, in alphabetical order, Acalvio, Attivo Networks, CounterCraft, and Zscaler.
- The Market Leaders in DDP are, in alphabetical order, Acalvio, Attivo Networks, Fidelis Cybersecurity, and Zscaler.


















































