1 Introduction
Access Management refers to the group of capabilities targeted at supporting an organizations' access management requirements traditionally found within Web Access Management & Identity Federation solutions, such as:
- Authentication
- Authorization
- Single Sign-On
- Identity Federation
These access management capabilities are well-established areas in IAM's broader scope (Identity and Access Management). They are continuing to gain attraction due to emerging requirements for integrating business partners and customers.
Web Access Management (WAM) & Identity Federation started as distinct offerings. (Web) Access Management is a rather traditional approach that puts a layer in front of web applications that takes over authentication and – usually coarse-grained – authorization management. That type of application can also provide HTTP header injection services to add authorization information to the HTTP header used by the back-end application. Also, tools are increasingly supporting APIs for authorization calls to the system. Identity Federation, on the other hand, allows splitting authentication and authorization between an IdP (Identity Provider) and a Service Provider (SP) or Relying Party (RP). The communication is based on standard protocols. Back-end systems need to be enabled for Identity Federation in one way or another, sometimes using the Web Access Management tool as the interface. Identity Federation can be used in various configurations, including federating from internal directories and authentication services to Cloud Service Providers or different organizations. However, most vendors today provide integrated solutions that support both a centralized access management based on federation protocols such as:
- SAML v2
- OAuth
- OIDC
Access Management focused IDaaS vendors vary from the traditional SSO vendors. Overtime, WAM vendors progressed to address most internal web-centric use-cases with greater customization flexibility according to business-specific requirements. Further progressions included vendor solutions born in the cloud that address standardized access management requirements for SaaS and IaaS applications. However, this came with some architectural limitations in how their solutions could be more easily extended to address access management for on-prem applications. Over the last few years, these vendors have made significant changes to their product architecture to make them cloud-ready or support extended to on-premises applications.
However, support for web applications without federation support through traditional approaches such as Http header injection or credential injection must still be considered. Both methods deliver a single sign-on (SSO) experience to the users across multiple web sites and allow for centralized user management, authentication, and access control.
These technologies are enabling technologies for business requirements such as agility, compliance, innovation (for instance, by allowing new forms of collaboration in industry networks or by adding more flexibility in the R & D supply chain), and the underlying partnership & communication.
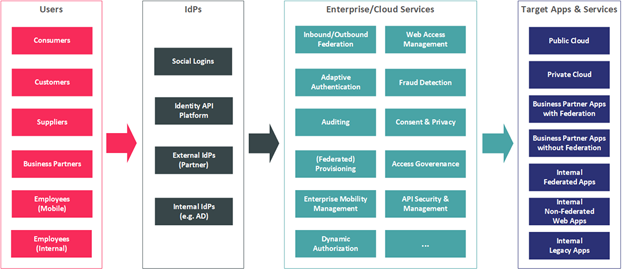
Although traditional on-premises Access Management solutions have focused on WAM & Identity Federation solutions in the past, KuppingerCole sees a convergence of this market with Access Management focused IDaaS solutions. Therefore, this Leadership Compass considers Access Management solutions deployed on-premises, in the cloud, or as a hybrid model. Solutions offered as a managed service are also be considered when the technology is owned by the MSP (Managed Service Provider).
1.1 Market Segment
Access Management and Identity Federation are still frequently seen as separate segments in the IT market. However, when looking at the business problems to be solved, these technologies are inseparable. The business challenge to solve is how to support the growing “Connected and Intelligent Enterprise.” Businesses require support for business processes incorporating external partners and customers. They need access to external systems and rapid onboarding of externals for controlled and compliant access to internal systems. They request access to external services such as Cloud services, as well as capabilities to use their acquired access data to drive intelligence within their systems. The required use of mobile devices is also leveraged onto organizations as the changing workforce desires to work anywhere from any device. IT has to provide an infrastructure for this increasingly connected and intelligent enterprise, both for incoming and outgoing access, both for customers and other externals such as business partners, including existing and new on-premise applications, cloud services, and mobile devices.
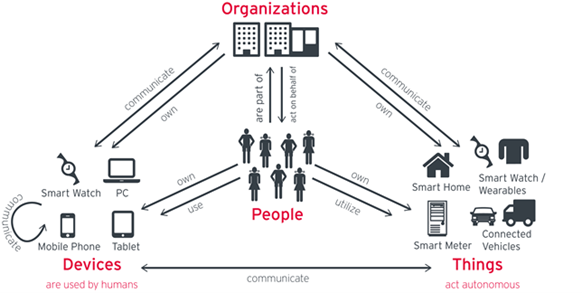
IDaaS Access Management (AM) offers a springboard for most organizations to start using foundational IAM elements delivered from the cloud and move the rest of the IAM functions, as they find it appropriate and at a pace that matches the organizational security maturity and cloud strategy. The IDaaS market, with its ease of adoption and cloud-native integrations, is slowly overtaking the on-premises IAM market.
The IDaaS AM market is continuing on a growth spree allowing these technology trends to speed up the adoption by aligning them to match the organization’s IAM priorities that security in which IAM leaders must take note. The IDaaS market continues to evolve with a significant push from organizations looking to adopt cloud-based delivery of security services, including IAM. With IDaaS vendors slowly bridging the gap with traditional on-premises IAM software in terms of depth of functionalities, they present a strong alternative for organizations to replace existing on-premises IAM deployments.
IDaaS is only delivered as SaaS, hosted, and managed by the IDaaS vendor itself. Vendors that use the on-premises software provided by other vendors to offer hosted and managed IAM services are not considered IDaaS vendors. Mostly combined in separate service bundles based on adoption and usage trends, most services are priced per managed identity or active users per month. Some functions such as user authentication or fraud detection can be charged on a per-transaction basis depending on the function’s delivery and consumption.
As an alternative to organizations managing the Access Management solutions themselves, some vendors provide offerings described as Managed Services, whether on-premises or Software as a Service (SaaS) offerings. Pure-play SaaS solutions are multi-tenant by design. Customers can easily onboard, usually as simple as booking online and paying with a credit card. On the other side, Managed Service offerings are run independently per tenant. The two aspects of the high relevance are the elasticity of the service and a pay-per-use license model.
Providers of CIAM solutions increasingly understand the business use-cases requirements of managing privacy policies, terms of service, and data sharing arrangements that change frequently and adapt their services accordingly. For organizations doing business across borders, it is important to offer functions that allow them to comply with data sharing and privacy regulations, such as consumer notification and consent management. There’s a varying level of support available from Access Management vendors to manage these CIAM functions.
The support for open identity standards shapes the direction and defines AM implementations' success increasingly. This also drills down to the sense that an organization's ability to support business requirements through IAM depends on the AM vendor's flexibility to support both open industry standards and protocols. Support for Open Banking presents a great validation of that observation. Most popular authentication and identity federation standards include support for LDAP, Kerberos, OpenID, OAuth, SAML and sometimes RADIUS and TACAS. Organizations with a need for dynamic authorization management might require support for XACML or UMA. User provisioning services commonly require support for SCIM and SPML. Security and IAM leaders are encouraged to understand whether the service supports these standards OOTB or require customizations using available SDKs or other programmable interfaces. This will go a long way in keeping your IAM flexible and sustainable.
Increasingly we are seeing security platform APIs becoming more readily available, exposing the platform's functionality to the customer for its use. It's driven by the need to meet emerging IT requirements that include hybrid environments that span across on-premises, the cloud, and even multi-cloud environments. APIs are provided for the different functional requirements of IAM, Federation, IDaaS & CIAM, giving the ability to select these market segment capabilities a la carte as needed. Exposing key functionality via APIs allows for workflow and orchestration capabilities across environments and better DevOps support through automation. API-driven platforms diverge from the COTS solutions offered in the past and are defined by its use cases. Some use cases are targeted at organizations that, due to the complexity of internal processes and other operational reasons, are looking to build their own C/IAM platform, automate or enhance existing IAM capabilities. Also, where traditional turn-key COTS are primarily UI-driven, API-based platforms typically require a developer-ready solution, providing API toolkits such as widgets or SDKs that facilitate rapid development.
Fraud is a major cost to businesses worldwide. As one would expect, banking, finance, payment services, and retail organizations are some of the most frequent fraudsters' objectives. However, insurance, gaming, telecommunications, health care, cryptocurrency exchanges, travel and hospitality, and real estate are increasingly targeted as cybercriminals have realized that most online services trade in monetary equivalents. Moreover, after years in the sights of cybercriminals, banking, and finance, in general, are better secured than other industries, so fraudsters attack any potentially lucrative target of opportunity. Fraud perpetrators also continually diversify their Tactics, Techniques, and Procedures (TTPs). Although Fraud Detection solutions, also referred to as Fraud Reduction Intelligence Platforms (FIPS), is often considered a different market with its separate offerings, there has been a noticeable up-tick in Access Management solutions providing some level of Fraud Detection capabilities. These capabilities range from the detection of identity fraud through Identity Proofing to the detection of unauthorized account takeover, response mechanisms, or support for user and device profiling as some examples. This Leadership Compass evaluates and reports on the level of Fraud Detection support for each vendor, giving the reader an indication of the extent of this trend in the AM market.
Besides these technical capabilities, we evaluate participating Access Management vendors on the breadth of supported capabilities, operational requirements such as support for high availability and disaster recovery, strategic focus, partner ecosystem, quality of technical support, and the strength of market understanding and product roadmap. Another area of emphasis is providing Access Management capabilities out-of-the-box, rather than delivering functionality partially through 3rd party products or services. Finally, we also assess their ability to deliver a reliable and scalable Access Management service with desired security, UX, and TCO benefits.


















































