KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.


Unlock the power of industry-leading insights and expertise. Gain access to our extensive knowledge base, vibrant community, and tailored analyst sessions—all designed to keep you at the forefront of identity security.
Get instant access to our complete research library.
Access essential knowledge at your fingertips with KuppingerCole's extensive resources. From in-depth reports to concise one-pagers, leverage our complete security library to inform strategy and drive innovation.
Get instant access to our complete research library.
Gain access to comprehensive resources, personalized analyst consultations, and exclusive events – all designed to enhance your decision-making capabilities and industry connections.
Get instant access to our complete research library.
Gain a true partner to drive transformative initiatives. Access comprehensive resources, tailored expert guidance, and networking opportunities.
Get instant access to our complete research library.
Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
In less than a decade, containers have undergone an impressive evolution: from a lightweight virtualization technology to the de-facto standard for software distribution to a powerful underlying platform for complex and distributed applications. For many organizations, container orchestration platforms like Kubernetes serve as a universal foundation for deployment, scaling, and management of applications that works consistently across on-premises and multi-cloud environments.
The growing demand for new software architectures has given rise to microservices that allow businesses to develop and deploy their applications in a much more flexible, scalable, and convenient way - across multiple programming languages, frameworks, and platforms. Microservices, containers, and Kubernetes have quickly become synonymous with modern DevOps methodologies, continuous delivery, and deployment automation and are generally praised as a breakthrough in developing and managing cloud-native applications and services.
Unfortunately, this massive change in infrastructure and a major increase in overall complexity (although much of it is hidden from developers thanks to multiple layers of abstraction and convenient tools) has introduced numerous new risks and security challenges as well as new skills needed to mitigate them efficiently.
Initial attempts to repurpose existing security tools for protecting containerized and microservice-based applications have quickly proven to be inadequate due to their inability to adapt to the scale and ephemeral nature of containers. Static security products that focus on identifying vulnerabilities and malware in container images, while serving a useful purpose, do not address the full range of potential risks.
The need to secure containerized applications at every layer of the underlying infrastructure (from bare-metal hardware to the network to the control plane of the orchestration platform itself) and at every stage of the development lifecycle (from coding and testing to deployment and operations) essentially means that container security has to cover the whole spectrum of cybersecurity and then some.
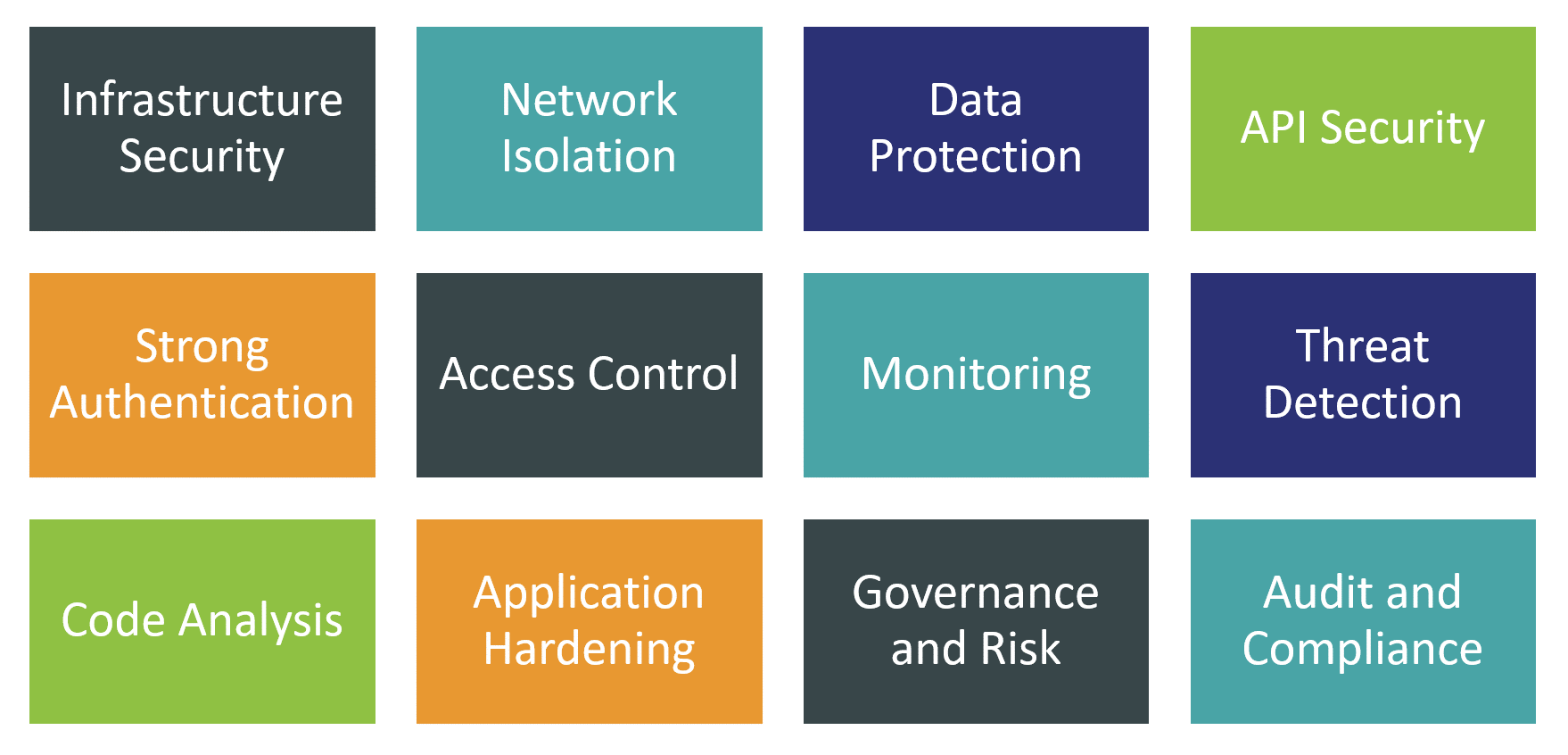
This is why for this Leadership Compass, we have decided to focus primarily on the universal container and Kubernetes security platforms, which aim to analyze, monitor, assess, and mitigate risks along the full lifecycle of application containers - starting with developing, testing, and hardening container images to runtime monitoring and threat detection to responding to identified security incidents. At the same time, we expect container security solutions to expand their coverage to multiple layers of infrastructure including hardware, host OS, virtualization, and networking layers.