1 Introduction
While SAP solutions remain an important element of the business application infrastructure of many organizations, these are increasingly complemented by other vendor’s solutions. Managing access entitlements including roles, but also SoD (Segregation of Duties) rules, firefighter access, and other aspects around identity, access, and security is essential for protecting these business-critical applications.
Many critical business systems are following the trend of shifting to the cloud, using either solutions provided by SAP such as SuccessFactors or Ariba, or to other vendors’ solutions. Thus, the scope for centralized access controls is expanding beyond the traditional ABAP systems and even beyond SAP. The requirements for solutions are expanding, either by supporting a broader range of systems or by delivering adequate integration points with other solutions covering, e.g., SaaS applications.
Although there are many other systems in place which also contain critical information, many businesses still rely on the availability of well-designed and well-protected SAP Systems. Traditionally, SAP systems are a major focus area for internal and external auditors. For the successful implementation of adequate controls, it essential that all Line-of-Business (LoB) systems are covered by an effective solution for managing risks, and within that for managing access control and SoD controls and implementing adequate Access Governance.
The segment is expanding in two directions:
- Breadth of supported environments, e.g., SAP Business Suite, SAP HANA and S/4HANA, and business applications that are provided as SaaS applications (Software as a Service) by SAP as well as by other vendors such as Workday, Salesforce, Microsoft, Oracle, and many others, with the expectation that solutions deliver strong support for SAP environments, but also support the broadening range of LoBs in use by organizations.
- Breadth of capabilities, beyond just identifying critical entitlements and SoD violations to a broader scope of mitigating access-related risks in such environments.
Deployment models for both the managed services and the solutions is changing, with more SaaS services to manage, and deployment in different ways – as ABAP solution, with SAP Fiori user interface, or separately from SAP as web applications or, becoming the new standard, as SaaS services.
The core of functionality remains in the management of access controls including critical entitlements and SoD conflicts in SAP and other LoB environments. However, solutions frequently also cover additional features such as break-glass access management (firefighter, emergency access), user lifecycle management, role optimization, and more. In this Leadership Compass, we put a strong focus on both the core capabilities and add in features.
These technologies are commonly referred to as Access Control Tools, Application Access Governance, or Application Risk Management. Focus of these solutions is in mitigating access-related risks in LoB environments.
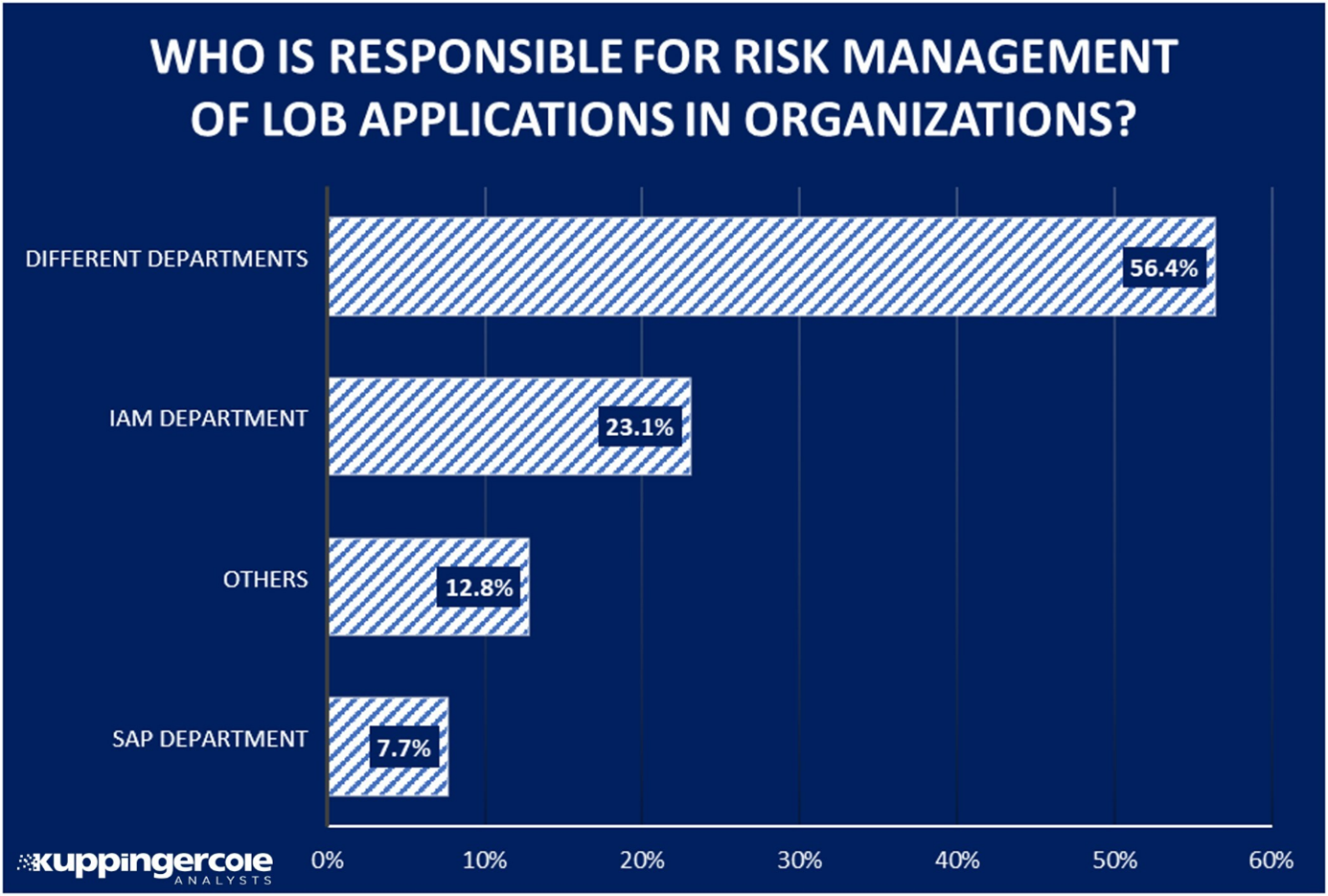
Figure 1: Risk Management and Security are still not handled consistently in organizations.
Saviynt is an established vendor in this market segment, covering a broad range of IAM capabilities with a strong footprint in both IGA and specialized Application Access Governance.

















































