1 Introduction
Contemporary business operations encompass a multitude of interconnected networks, devices, assets, and individuals. At the same time, a substantial portion of a company's workforce comprises contractors, partners, seasonal workers and vendors. Effectively managing these identities and regulating access presents a complex challenge, necessitating an all-encompassing solution to bring these crucial non-employee identities under control.
Many organizations have strategic shortfalls in third-party risk management governance. Specifically, only 42% of respondents say managing outsourced relationship risk is a priority and only 40% of respondents say there are enough resources to manage these relationships.
(RiskRecon/Ponemon Institute September 2022)
For some time, Identity and Access Management (IAM) platforms have empowered IT security and compliance managers to govern internal system access. Without IAM, administrators had limited visibility regarding the identities accessing resources either on premises or within private clouds. Privileged Access Management (PAM) extended this control by regulating access to sensitive administrative tasks and high-value data assets.
However, modern organizations also need to accommodate external identities. This is particularly relevant for companies operating in the B2B, B2G, and B2B2C sectors with intricate supply chains and supplier/customer/partner relationships. The mix includes important actors within the supply chain, such as contractors, freelancers, and external auditors. It is crucial for the hosting or sponsor organization to have the means to regulate secure access centrally. The complexity increases when considering that suppliers have their own connections to partners and supply chains (known as “fourth parties”), which can further impact the sponsor organization.
According to the Ponemon Institute, 54% of respondents indicate that their organizations lack a comprehensive inventory of all third parties with network access, while 65% have not identified the third parties with access to the organization's most sensitive data. Furthermore, the same report reveals that 51% of organizations experienced a data breach caused by a third party in 2021.
There are several business problems that the unmanaged growth of non-employee identity presents. One is that managers and auditors do not have an accurate count of non-employee users or a clear understanding of the information they can access. It is also hard to determine whether a user is an employee, a contractor, or third-party supplier. There can be issues when a former employee returns to the organization as freelancer or when a contractor becomes a full-time employee.
Duplicate user accounts and multiple credentials are a big problem which can also result in multiple software licenses being created for the same user. Some organizations try to solve these issues by improving or modifying HR software tools – often with limited success, as these are very much focused on HR issues and HR workflows. Others may try developing a proprietary platform which often proves to be costly and time-consuming and tends to tie up valuable resources. All too often organizations simply do not have the correct IAM processes, policies, and software in place to cover all types of identities that require access to complete business workflows and tasks.
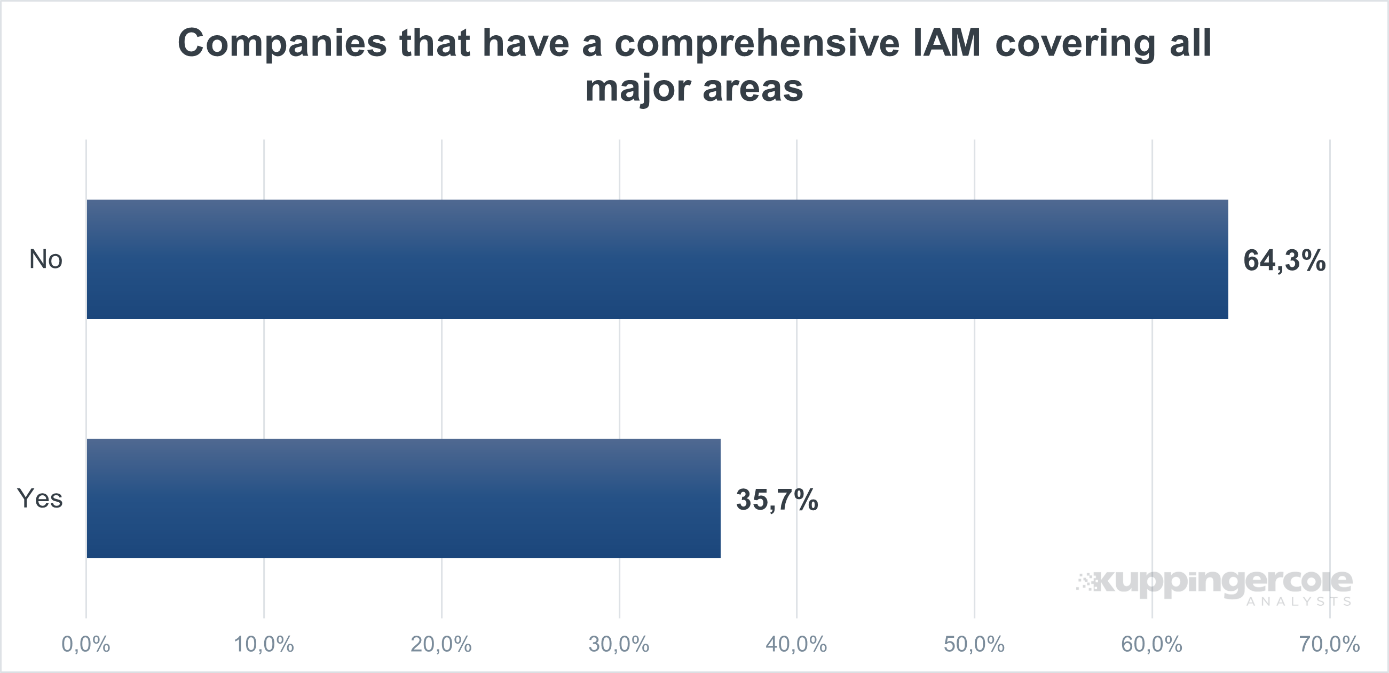
Figure 1: A survey of identity practitioners shows that organizations are not utilizing IAM for newer identity types. (Source: Kuppinger Cole Analysts)
While certain IAM and PAM platforms allow limited access for third parties, many do not, requiring specialized software to govern supply-chain access. Therefore, software has been designed to facilitate secure access and collaboration throughout the multiple tiers of an organization's supply chain and partners.


















































