1 Introduction
Data is the most valuable asset of the modern organization but protecting and controlling it when migrating to cloud services is a major challenge. Data protection and data sovereignty laws and regulations are growing around the world, and organizations face substantial financial penalties if they fail to navigate this landscape of competing and sometimes contradictory requirements. Data protection platforms can help organizations to secure their data and meet their regulatory obligations by controlling the data throughout its lifecycle.
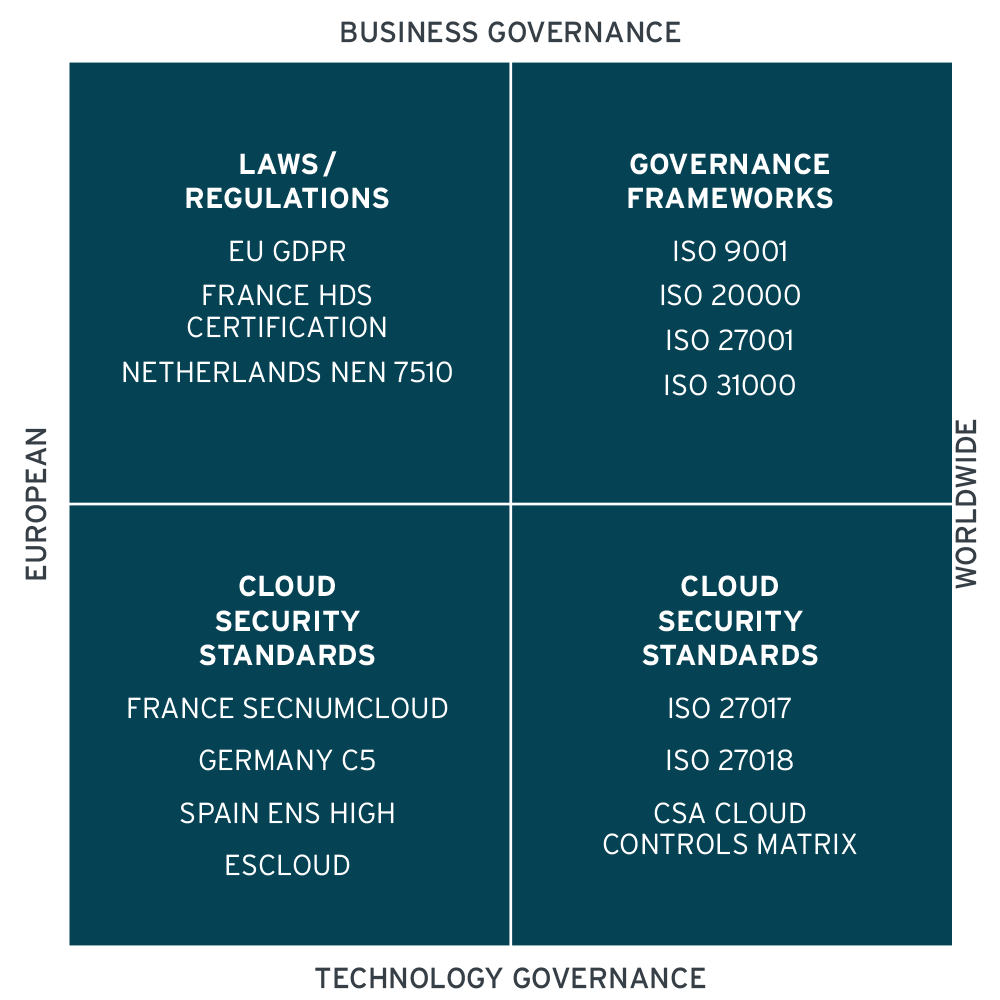
Figure 1: Examples of Cloud Security Standards and Frameworks from Around the World
Organizations are using cloud services to transform the way they operate, improve flexibility, innovate, and reduce costs. However, there is a tension between the benefits that these services provide and the risks from using a third party, often in another country, to process data. In addition, organizations hold significant amounts of data across a wide range of systems and environments as well as clouds. Governing, controlling, and securing this data in a consistent way wherever it is held is a major challenge.
Cyber threats as well as misuse and mistakes create three major business risks for organizations that do not secure their data. An organization that cannot access business-critical data because of ransomware or denial of service attacks could fail. If an organization’s intellectual property is stolen and given to a competitor, it could lose its competitive advantage. If the personal data that an organization holds is breached through a cyber-attack or unauthorized access it would face financial penalties as well as reputational damage.
Data protection legislation across the world has led to wide ranging controls over the movement of data. A notable example of this is the EU General Data Protection Regulation (GDPR) further clarified by the European Court of Justice Schrems II Judgement and the subsequent recommendations by the EDPB (European Data Protection Board). While these recommendations apply to the protection of the personal data of EU residents, they are equally relevant to the protection of all sensitive data.
This judgement and the EDPB recommendations make it clear that processing the personal data of EU residents in the clear by cloud service providers and other data processors located outside of the EU is not permitted and that legal safeguards such as SCCs (Standard Contractual Clauses) are not sufficient. Organizations must implement supplementary technical measures to protect that data. The recommendations identify three major technical measures with examples of how they can be applied in several use cases. In summary these are encryption, pseudonymization, and split processing.
Organizations must govern their data whatever its form and wherever it exists throughout their lifecycle. This includes discovering and classifying data according to its sensitivity. Making authorized access easy while ensuring privacy and protecting against illegitimate use can be seemingly conflicting goals. Organizations must ensure data resilience in the face of cyber-attacks as well as natural disasters. Finally, data must be kept for only as long as it is needed and then securely disposed of at the end of its life.
Modernization through migrating to the cloud increases the challenges and organizations should choose their data protection platform to meet these challenges.


















































