1 Introduction
Enterprise-level companies today have the challenge of understanding their security posture amid proliferating devices, applications, and data. To understand the potential risks, a systematic approach is essential for identifying, assessing, and mitigating threats to an organization's information systems and data from cyber threats. Risk identification includes evaluating potential threats and their likelihood of occurrence and understanding the potential impact of a successful cyber-attack. Once the risks are identified, potential impact and likelihood need to be quantified and prioritized based on severity, considering the value of the assets at risk and the possible consequences of a successful cyber-attack. Effective risk mitigation is achieved through the implementation or modification of robust technical controls. As cybersecurity threats are dynamic and ever-evolving, continuous monitoring of the implemented controls becomes crucial. It is essential to remain vigilant and stay abreast of emerging threats and vulnerabilities, ensuring that the security measures are always up-to-date and capable of safeguarding against the latest risks.
Vulnerability Management and Risk Management are closely related. Both practices take a proactive approach to security, although Vulnerability Management seeks to identify vulnerabilities before attackers can exploit them and takes steps to mitigate or eliminate them. Both methods also involve assessing and prioritizing identified vulnerabilities or risks, and Vulnerability Management assesses vulnerabilities based on their severity, potential impact, and exploitability. In Vulnerability Management, the goal is to remediate or mitigate vulnerabilities by applying patches, updating or deleting software, making configuration changes, or deploying additional security controls. Both practices acknowledge that vulnerabilities and risks can change over time, and therefore, they need to be consistently evaluated and addressed to maintain an effective security posture.
Another challenge organizations face today is maintaining endpoint compliance with the required standards, regulations, and best practices. This may include laws like the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), or industry-specific standards like the Payment Card Industry Data Security Standard (PCI DSS). Compliance Management also involves risk assessments, developing appropriate security policies and procedures, implementing suitable security controls, and continuous monitoring and auditing. Measures must be in place to protect sensitive data, prevent unauthorized access, and mitigate overall cybersecurity risks.
A third challenge is when an organization has security-related data in multiple information systems throughout the company when evaluating potential security risks. Integrating data into a centralized security posture view can be problematic when that data is distributed across those various systems. Monitoring, detecting, and responding to security incidents can also be more difficult when data is scattered across various systems. Also, sharing data between multiple systems can introduce complexities in managing access controls and permissions and issues involved when different information systems have different technologies, protocols, and interfaces. Integrating and ensuring compatibility between these systems can also be complex, potentially introducing security vulnerabilities during the integration process, and potential misconfigurations or vulnerabilities in one system may have unintended consequences on the security of interconnected systems.
With a single source of data related to assets within a comprehensive view, it becomes easier to holistically identify and assess and manage potential security risks and vulnerabilities – in real time.
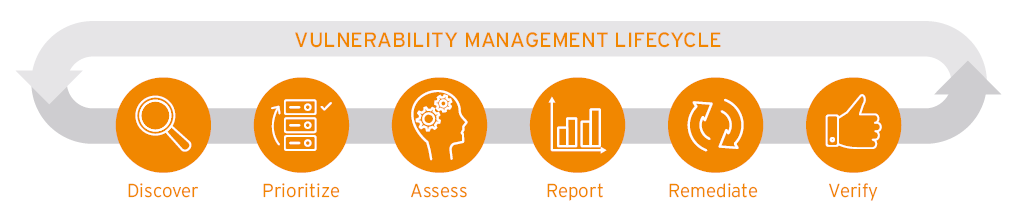
Figure 1 KuppingerCole vulnerability management cycle


















































