1 Introduction
Organizations depend on Line of Business (LoB) applications to support their operational processes, spanning all areas from finance to supplier management, CRM (Customer Relationship Management), HR (Human Relations) and many others. While SAP plays a dominant role in this market, most organizations don’t have a single vendor environment. There are several other players with comprehensive offerings, specialist vendors for certain domains, emerging vendors delivering SaaS solutions, and vendors targeting the SMB and mid-market.
Specifically the growth in SaaS adoption has led to fundamental changes in this market, with more and more organizations following a multi-vendor strategy for their LoB SaaS services. Also, SAP has acquired a range of SaaS services that have different architectures and security models than the SAP core platforms such as SAP ECC or S/4HANA.
With LoB applications supporting the core business processes, these take a critical role and must be well-protected. They also are subject to a variety of regulations, in specific financial management applications and the ones that are handling customer data. Thus, solutions that manage access to these applications, enforce SoD (Segregation of Duties) rules, and control emergency access are essential here.
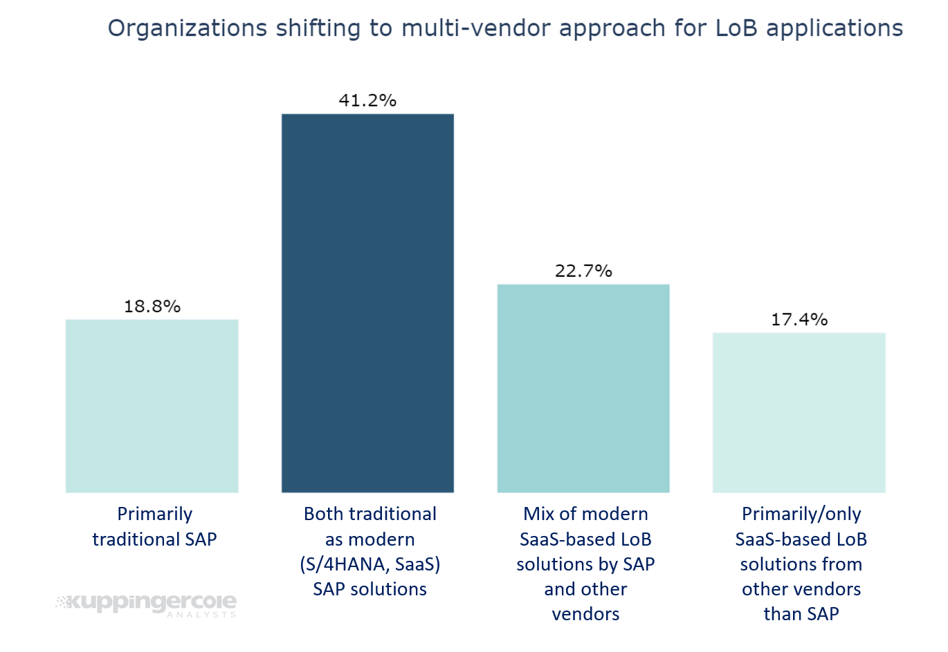
Figure 1: While many organizations still have a strong SAP installed base, a growing number is deploying other vendor’s LoB solutions in addition.
Due to the heterogeneity of the LoB market, this increasingly requires solution that are not just supporting SAP ECC and S/4HANA in depth, but also other LoB applications. A challenge therein is that these applications come with a wide range of entitlement models, some of these being very complex and consisting of multiple tiers. SAP, for instance, has, amongst others, concepts such as business roles, single roles, authorization objects, and transactions in place. Complexity is further increased by newer models such as Fiori specific entitlements. These specific models found in SAP and other LoB applications require in-depth support.
On the other hand, there are many business processes spanning multiple applications and SaaS services. SoD rules must be able to not only identify SoD violations within a LoB application, but also for cross-application processes. This requires a certain degree of unification across the various LoB applications in place, while still supporting and understanding the specifics of the various applications. It also requires that the SOD ruleset be easily maintained or dynamically adjust to changes to business processes. The ruleset must also be able harmonize configuration differences across instances of the same application.
To further complexify this situation, it is not just about LoB applications, but also other types of services such as file storage or office applications that must be considered. LoB and SAP access control solutions no longer can be segregated from IGA (Identity Governance & Administration) solutions that serve the needs for identity lifecycle management, user provisioning, and access governance for other types of applications. IGA anyway commonly supports some of the LoB applications such as Salesforce or the Oracle eBusiness Suite. An integrated approach is required that goes well-beyond SAP and takes a broader perspective.
Only when both the depth of application controls and the breadth of application coverage are adequately managed can key capabilities such as role design, access analysis and certification, risk management, or user provisioning can be implemented efficiently in an organization.
The market for solutions that support access control and “GRC” (Governance, Risk Management, Compliance) for SAP and other LoB applications is under change. Solutions that cover products of a range of vendors are becoming the norm. Integration to IGA solutions or integrated IGA capabilities also are regularly found. Additionally, several of the solutions expand beyond access control into a certain level of process controls and transaction controls, thus supporting CCM (Continuous Controls Management) approaches.

















































