1 Recommendations
Product security is as much about opportunity as it is about protection. The Internet of Things (IoT) brings limitless possibilities, but almost as much security risks.
Don't wait for all-encompassing IoT security solutions or standards to become available before implementing security into IoT products. Although, it can be an unrealistic expectation to apply all of the existing enterprise security measures employed today to IoT devices that have their unique and constrained characteristics different from the desktop software in the current environment. The IoT ecosystem is complicated, and no silver bullet can mitigate all the threats, but a few principles can go a long way in helping with product security while the IoT landscape continues to develop.
Data
Principally in industrial IoT, an organization should always protect intellectual property as if it were Top Secret information – the life of a business depends on it. Where constrained devices allow, encrypt, restrict access and, where you trust, make sure you verify with logging and monitoring.
Patching
Provide a mechanism for software updates and security flaw patches. IoT vulnerabilities need to be mitigated promptly, moreover in industrial settings.
Privacy
To a greater extent for consumer IoT products that collect user information, use privacy by design principles. The EU General Data Protection Regulation (GDPR) will ensure that organizations take data privacy into account.
Protocols
Although there are a plethora of protocols that can be used, steer away from proprietary or develop your own. Use standard protocols that are well established and validated by communities of practice that have worked to mitigate vulnerabilities over time.
Training
There are a minority of developers that have strong security experience. Invest in security awareness and training.
Often an organization will feel the pressure to release products quickly in the speed to market but may end up compromising on security. Instead of applying security as an add-on feature after deployment, adopt Security by Design (SbD) in the early stages of the IoT projects by involving security professionals at the start. The earlier security departments are included in the project process, the higher the return on investment (ROI).
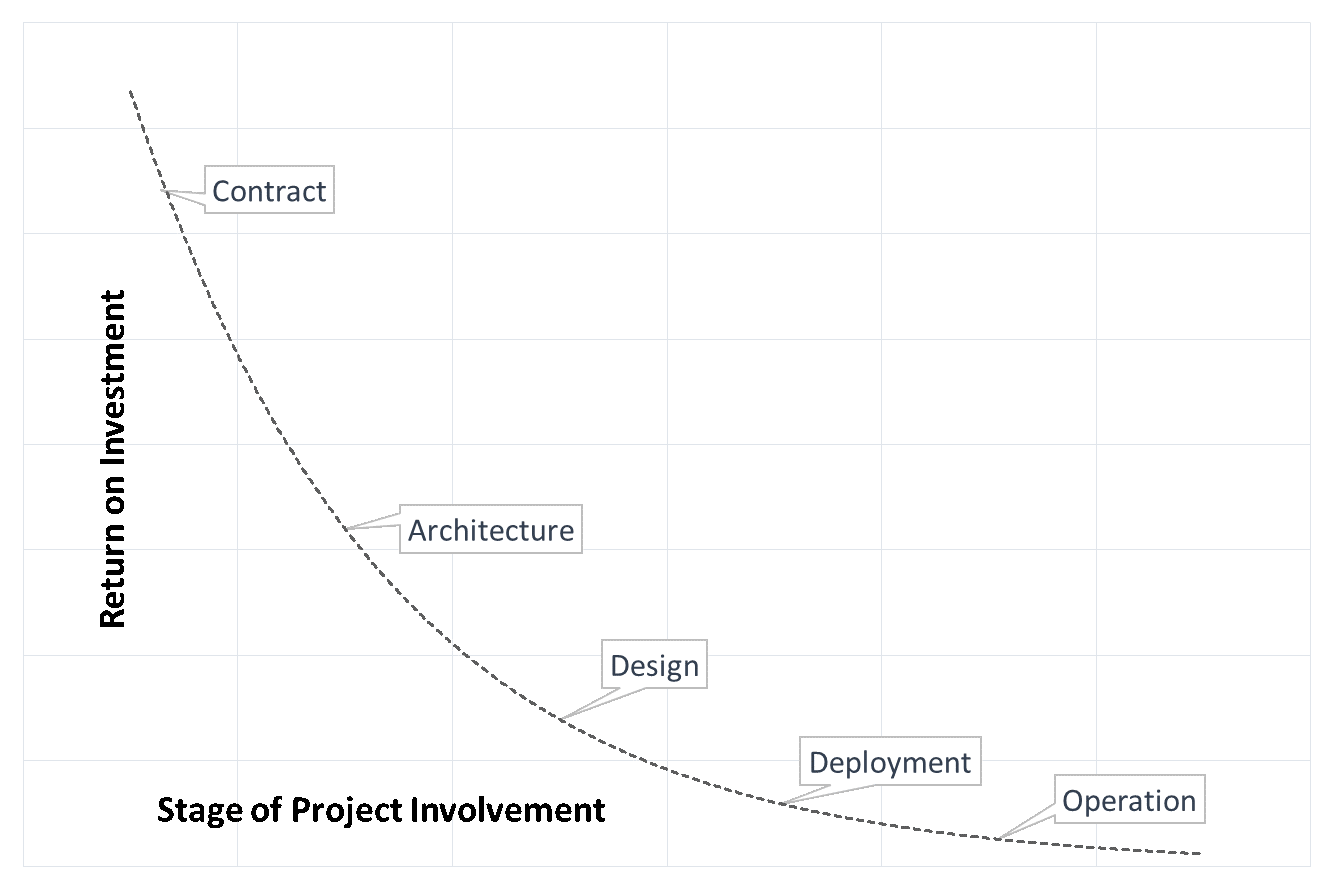
Get this right from the beginning, and it will not matter what product uses come later, they will more likely be secure.
















































