1 Introduction
As more and more companies are embracing digital transformation, the challenges of securely storing, processing and exchanging digital data continue to multiply. With the average cost of a data breach exceeding $3.9M, just direct financial losses can be catastrophic for many companies, not even considering indirect reputational damages. High-profile “mega-breaches” that expose millions of sensitive data records can easily drive these costs up to hundreds of millions of dollars, but even the victims of smaller ones are now facing increasingly harsh compliance fines – consider the recent decision to fine British Airways £183 million for exposing their customers’ data last year.
It is therefore completely unsurprising that both corporate executives and government policy-makers now consider data protection their top priority. According to Oracle’s Security in the Age of AI report, 45% of policy-makers cite data security as their biggest concern, and over 60% of surveyed professionals consider security the top benefit of cloud technology.
Just keeping track of all the digital information is a big problem, but understanding which data is more sensitive according to various policies and regulations and then selecting and enforcing the necessary data protection and governance capabilities is already too much even for the largest businesses. Indeed, many would love to outsource parts of this responsibility to a qualified third party like a cloud service provider.
However, as anyone familiar with the shared responsibility model adopted by most Cloud Service Providers (CSP) would quickly realize, even though customers no longer need to worry about the underlying infrastructure security, they still retain full responsibility for any security or compliance violation involving their data and users. From sensitive data discovery and classification to access governance and activity monitoring to user risk assessment and management – all these functions are crucial for comprehensive and continuous data protection, yet none of these are provided out of the box by a cloud service provider.
The way Oracle attempts to solve these challenges for their customers is a direct consequence of their radically different, but still unique position in the database and cloud markets. As a latecomer to the Infrastructure-as-a-Service market, the company had a chance to learn from the requirements of their enterprise customers and implement many data security and compliance controls directly in Oracle cloud services.
The company takes a lot of pride in their 2nd generation cloud infrastructure, which was designed from scratch according to the Security-by-Design principle with a higher degree of isolation than any other major CSP, providing better network security, threat containment, and access governance. To benefit from the strict network-level separation of cloud servers from the control plane, customers do not need to do anything – they can expect that their data in use isn’t just physically isolated from other tenants, but from Oracle’s own administrators as well.
The Oracle Autonomous Database introduced an automated self-tuning and self-patching cloud-based database platform that fully eliminates administrative user access, strictly enforcing separation of duties and adhering to the latest DB security best practices.
Autonomous Database customers also inherently benefit from critical data security and governance controls like data encryption enabled by default; secure backup; no cloud administrative access to data; automated upgrade, backup and performance tuning; and other database security measures that are integrated into the Oracle Database.
These developments alone have largely taken the burden of securing the underlying infrastructure and database platform itself off the customer’s shoulders. Yet, even the Autonomous Database cannot completely ensure security and appropriate usage of corporate data. Security depends in part on appropriate usage, and the underlying database and the infrastructure lack the business context associated with customer’s data, user identities, corporate policies and other key factors that influence risk assessment and prioritization. There is still a need to identify and classify the types of data loaded into a database, review privileges of the users granted access to the data and validate that access to sensitive data is in accordance with corporate policy.
And this is where the recently released Oracle Data Safe comes into play. With this integrated cloud-based service for automating data governance and risk management activities, the company has further expanded its security portfolio to ensure that customer’s sensitive data remains secure.
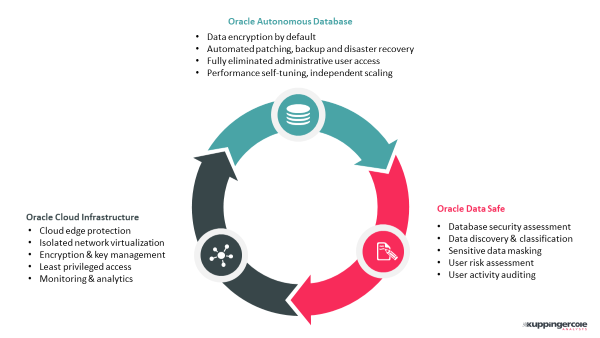
And while activities like data discovery and classification or user monitoring and risk assessment still fall under the customer’s responsibly, with Data Safe they now have a convenient tool that provides guidance, support and automation for protecting sensitive data from security threats and compliance violations – at no additional cost for their databases in the Oracle Cloud.


















































