1 Introduction / Executive Summary
The landscape of enterprise and personal computing technology is continuously evolving. It didn't seem that long ago, where the work environment consisted of a desktop computer and a landline phone. Traditional management of the desktop computers relied on manual updates of software and patches that were layered on top of each other. Later, "Gold Images" of desktop operating systems were used to provide a good know state of the OS but still required patches on a routine schedule, which would become what was known as traditional management.
As mobile phones became economically available, laptops and tablets computers replaced many stationary desktop computers; the business could control the employee device regarding it's OS and software applications used as well as security controls when the device was within the perimeter of the organization. Client management tools were used to manage these environments. Client management involves capabilities such as OS deployment, software distribution, patch management, monitoring, and remote-control tools to support administration or to help automate other support functions that are typically executed manually.
Later, organizations needed to quickly deal with the introduction of the bring-your-own-device (BYOD) paradigm shift. Organizations required policies to define the boundaries of BYOD that included the ability to segregate the business data and applications from personal data and applications. Mobile device management (MDM) provided the tools to control the device functionality and help manage the lifecycle of these mobile devices and their platforms. Enterprise Mobility Management (EMM) solutions added mobile information as well as application and content management. The ability to push software, updates or patches to devices has become what is known as modern endpoint management.
Since then, work environments have continued to change. The range of endpoint device types have expanded past desktop, laptop, tablets, and mobile phone to now include printers, IoT devices, wearables like Apple Watch, and even newer types of endpoint devices that support virtual/augmented/mixed reality environments using headsets such as Oculus and HoloLens. Businesses are seeking to improve productivity and efficiency, while employees want to work from anywhere at any time. And with the more recent Covid-19 world we live in today, the requirement to work from home has become imperative, which requires the use of mobile devices to access enterprise applications and data as if they were in the office.
Given the complexity and growing number of different types of technologies involved in linking employees to corporate data both on-premises and in the cloud, mobile device management has gone through several iterations and approaches, with many enterprises now standardizing on a Unified Endpoint Management (UEM) approach.
This KuppingerCole Leadership Compass provides an overview of vendors and their product or service offerings in a certain market segment. This Leadership Compass focuses on Unified Endpoint Management from vendors from more localized geographic regions to vendors with a global presence. It considers these services in the context of the hybrid, on-premises, and cloud, with IT services delivery models commonly now found in enterprises.
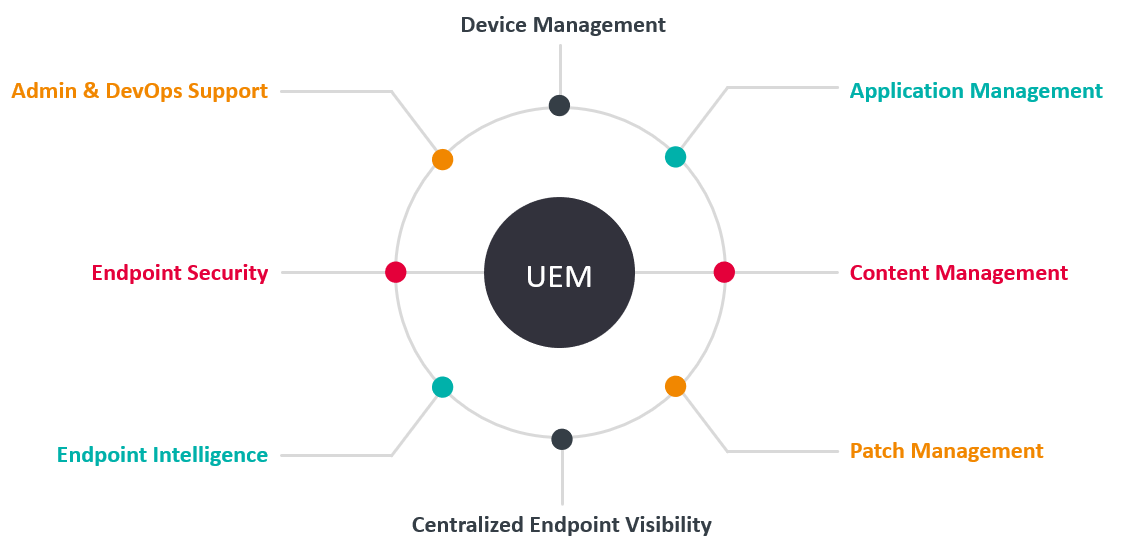
1.1 Highlights
- This Leadership Compass evaluates over 60% more UEM product vendors over the previous years.
- The UEM market is growing, and although maturing it continues to evolve.
- UEM is essential to business as a strategic approach to ensure overall IT security in a hybrid work environment.
- The level of endpoint intelligence has become a key differentiator between UEM product solutions.
- Device and Patch Management are the two strongest capabilities for the majority of products evaluated in this Leadership Compass.
- Varying levels of Application and Content Management appear as differentiators between UEM product solutions.
- The Overall Leaders are (in alphabetical order) Citrix, Entgra, IBM, Ivanti, ManageEngine, Matrix42, Microsoft, VMware.
- The Product Leaders (in alphabetical order) are Citrix, Entgra, IBM, Ivanti, ManageEngine, Matrix42, Microsoft, VMware.
- The Innovation Leaders (in alphabetical order) are Citrix, Entgra, IBM, Ivanti, ManageEngine, Matrix42, Microsoft, VMware.
- Leading vendors in innovation and market (a.k.a. the "Big Ones") in the UEM market are (in alphabetical order) Citrix, IBM, Ivanti, ManageEngine, Microsoft, VMware.


















































