1 Introduction
Identity Governance and Administration (IGA) combines the traditional User Access Provisioning (UAP) and Identity and Access Governance (IAG) markets. While many vendors today offer combined capabilities to qualify as IGA vendors, a few, especially the new entrants, provide either Identity Provisioning or Access Governance capabilities to cater to specific needs of the organizations.
The IGA vendors differ in the depth and breadth of functionalities offered and thus can be classified as either provisioning or governance focused. This KuppingerCole Leadership Compass provides an overview of the IGA market with notable vendors and their products or service offerings in the market.
From our interaction with organizations of varied IAM maturity across the industry verticals, we note that while some are still looking for an Identity Provisioning solution with limited or no Access Governance capabilities, many others demand a strong Access Governance solution. The latter is mostly the case when organizations already have Identity Provisioning in place or when their starting point is Access Governance. One of the adoption patterns we have observed in the market is where fulfilment through Identity Provisioning is achieved via a managed service, and Access Governance is run by and within the organization itself to retain absolute control over governance functions. There are several other adoption patterns witnessed in the market where customer’s immediate requirements are limited to either Identity Provisioning or Access Governance but do not demand an IGA solution. In most other cases where there is a need for both, IGA products are preferred over provisioning or governance ‘only’ solutions to achieve the desired mix of capabilities. This is generally true for greenfield IAM implementations that have a need for both Identity Provisioning and Access Governance capabilities. It is important that organizations scope their IGA requirements well before starting to evaluate IGA products that differ in the strength of IGA functionalities making most of them better aligned for either provisioning or governance focused deployments.
Based on the adoption trends, changing customer priorities and deployment patterns, we decided to create two distinct Leadership Compass documents to help security leaders identify relevant IAM market segments and subsequently shortlist most appropriate technology vendors based on their immediate IAM priorities:
- LC Access Governance: This Leadership Compass focuses primarily on Access Governance and Intelligence capabilities, with required integrations into own or third-party entitlements and/or account repositories. We look at complete IGA offerings here too if they have strong Access Governance & Intelligence capabilities.
- LC Identity Governance and Administration: In this Leadership Compass, the primary focus is on the vendors that offer both Identity Provisioning and Access Governance capabilities, either as a common product or separate but integrable product components to deliver capabilities across the IGA spectrum.
These two LCs are complemented by two other Leadership Compass documents – LC IGA for SMBs (small and midsize businesses) that identifies and focuses on functional and operational IGA requirements of SMBs that are different in both objective and magnitude than large organizations. The other Leadership Compass is LC IAM Suites that focuses on comprehensive IAM suites and evaluates vendors for their completeness and functional depth of IAM portfolios to include core and even adjacent IAM capabilities such as Privilege Management, Enterprise SSO, Identity Federation, Web Access Management, API Gateways, Fraud Detection and Prevention etc. in addition to IGA as an integrated offering.
With these various LCs, we aim to provide CISOs and security leaders responsible for IAM the most practical and relevant information that they need to evaluate technology vendors based on the specific use-case requirements, whether these are IGA-driven, provisioning focused, governance focused, focused on comprehensive IAM suites or a combination of these.
1.1 Market Segment
Identity Governance and Administration refers to the increasingly integrated Identity Provisioning and Access Governance markets. Where Identity Provisioning focuses on tasks related to administering access fulfilment and entitlements throughout an identity life-cycle, Access Governance provides necessary (mostly self-service) tools for business to manage workflows and access entitlements, run reports, access certification campaigns and SOD checks. Access intelligence is the analytics layer over Identity Provisioning and Access Governance that offers business-related insights to support effective decision making and potentially enhance governance.
While Identity Provisioning remains a core IAM requirement, Access Governance is becoming a more sought-after capability for organizations requiring better visibility of identity administration and access entitlements across its IT infrastructure. Governance moves beyond simple reporting and dashboarding to offer advanced capabilities that include machine learning techniques enabling pattern recognition to deliver valuable intelligence for process optimization, role design, automated reviews and anomaly detection.
IGA concerns the capabilities in IAM market that broadly deal with end-to-end identity life-cycle management, access entitlements, workflow and policy management, role management, access certification, SOD risk analysis, reporting and access intelligence. As IGA becomes an important security risk and management discipline directly impacting the security posture of any organization, a lack of basic IGA capabilities can leave organizations exposed to risks originating from inefficient administration of identifies and access entitlements, poor role management and lack of adequate auditing and reporting. These risks range from identity thefts to unapproved and unauthorized changes, access creeps, role bloating, delays in access fulfilment, orphan roles and accounts, SOD conflicts leading to occupational and other internal frauds. Several incidents in recent past have emphasized the need to have better IGA controls for organizations of all sizes, across all industry verticals.
Identity Governance and Administration (IGA) products support the consolidation of identity information across multiple repositories and systems of record such as HR and ERP systems in an organization’s IT environment. The identity information including user accounts, associated access entitlements and other identity attributes are collected from across the connected target systems for correlation and management of individual identities, user groups as well as roles through a centralized administration console.
The IGA products are primarily aimed at supporting the following activities in an organization:
- Automated provisioning and de-provisioning of user accounts across nominated target systems
- Synchronization of identity attributes and access entitlements related to user accounts and groups across the identity repositories
- Management of access entitlements and associated roles of users across the IT environment
- Configuration and enforcement of static as well as event-driven access policies for the accounts to access the IT systems and applications
- Allowing users to validate their access to systems and applications, reset the passwords and create new access requests using self-service options
- Verification and synchronization of user account passwords and other identity attributes from an authorized event and source across the identity repositories
- Reconciliation of access across the IT environment based on defined policies to ensure compliance and prevent SOD and other policy violations
- Supporting on-demand and event-driven user access certification campaigns to detect and mitigate access violations
- Auditing and reporting of access activities leading to critical information regarding service monitoring and optimization
Traditional IGA deployments in most organizations have been facing many challenges ranging from complex implementations and lengthy product upgrade cycles to maintenance of overly customized IGA product and a lack of support for emerging functional requirements. The disconnect between business and IT security functions is another big reason for failed IGA deployments. In many organizations, IT security is primarily driven by the need to meet regulatory compliance, resulting in an undesired shift of IGA priorities from administrative efficiency and better risk management to auditing and reporting. Security leaders focused on IAM must ensure they are able to demonstrate the success of IGA deployments early-on with initial deployment phases to build the credibility and gather necessary consensus required to support IGA initiatives among the IAM stakeholder community.
The IGA market has witnessed several trends over the last few years including a major shift in the product strategy and development roadmaps to provide in-built support for cloud applications. These advancements to support the cloud integrations are in two directions:
a) IGA vendors that have re-architected their products to offer an identity bridging capability to integrate with cloud providers using industry specifications. Some IGA vendors have partnered with specialty identity brokers to extend on-premises IGA capabilities to cloud applications. Such approaches are suitable for organizations with a decent on-premises IT footprint and requirements to support complex IGA scenarios for legacy on-premises applications.
b) IGA vendors that now offer a cloud IGA product that is cloud deployable with ready integrations with popular cloud applications as well as with standard on-premises applications. This approach is more suitable for organizations with a massive strategic focus on the move to cloud and looking at achieving the benefits of cloud IGA deployments such as shorter deployment cycles, faster upgrades and lower TCO in short term.
Increased adoption of cloud-based identity stores and directories such as Microsoft Azure Active Directory (AAD) has created additional pressure on IGA tools to support Out-of-the-Box (OOB) integrations with cloud services based on industry specifications such as SCIM. Many IGA vendors are already offering ready integrations with Enterprise Mobility Management (EMM) tools to offer support for mobile devices in an attempt to enhance user experience (UX) which has become an important differentiating criterion for organizations to evaluate an IGA product. Most IGA vendors have undergone a significant re-engineering effort to enhance their user and administrative interfaces but offering mobile support for critical IGA functions such as access certifications and request approvals is not on the priority list for many organizations because of the expected due-diligence required to be carried out to complete these tasks. Inaccurate access certifications and uncertain access request approvals resulting from the inability of users to conduct appropriate due-diligence on mobile devices can be disastrous to an organization's overall security posture in the long term. Many IAM and security leaders are therefore advocating against offering mobile support for such critical IGA functions to the business.
IGA integration with other enterprise systems such as IT Service & Support Management (ITSSM) tools as well as Privileged Access Management (PAM) tools have also become a norm in the industry and more than 80% of the IGA vendors in the market today either offer OOB integration or utilize the available APIs for the required integration. The integration with ITSSM tools, particularly ServiceNow, is a popular approach for organizations wanting to consolidate IGA user functions (access requests, password management etc.) with other enterprise helpdesk functions under a common user interface (UI) or portal for IT related requests. ServiceNow APIs can be used to integrate with the IGA product in the background for request fulfilment on the target system.
Integration of IGA with PAM tools is another trend that we see picking up aggressively in certain industry verticals, particularly the ones that are heavily regulated. There are a few integration points observed, but the integration of IGA workflows for privileged access certification as well as role-based access of administrators to PAM system are amongst the ones delivering immediate credibility and business value to organization’s IAM program.
There is also an increased emphasis on integrating IGA tools with User Behavior Analytics (UBA) and DAG (Data Access Governance) tools depending on the drivers and business value expected of such integrations. UBA tools can benefit from integration with IGA tools by consuming the user’s access activity such as authentication and authorization information across IT applications and systems to establish and continuously update user access patterns based on their role and peers’ group. Similarly, DAG tools can benefit from IGA integrations by consuming user identity and access entitlement information and in turn offer contextual information on device endpoint and data residing on the device and other sources to the IGA tools for better policy management.
Some IGA vendors have ramped up their efforts to align their product development roadmap with DevSecOps initiatives of organizations to support containerized deployments. With an increasing demand in the market for IAM Microservices delivery, more and more IGA functions will be grouped based on the functional objectives and usage patterns to be delivered as microservices.
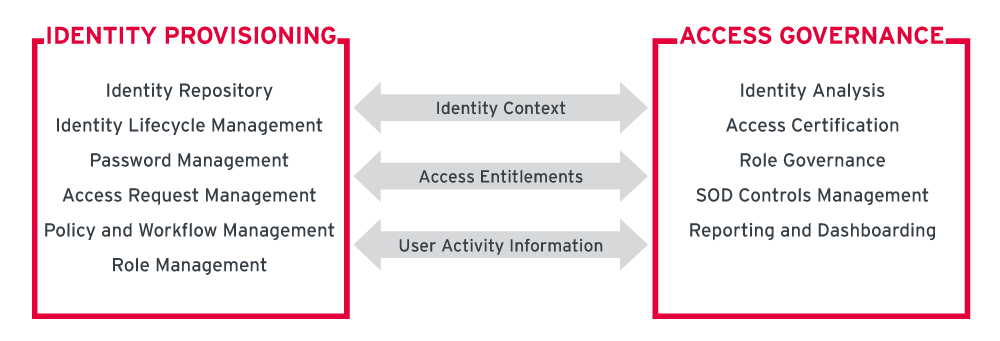
At KuppingerCole, we have identified the following as core capabilities delivered by the IGA vendors, primarily grouped under two product categories: Identity Provisioning and Access Governance.
Identity Provisioning:
- Identity Repository: Identity repositories are a core component of an IGA deployment and provide a mechanism to manage the identities, identity attributes, access entitlements and other identity related information scattered across the IT environment. Management of access rights information and other entitlements across the identity repositories are captured and correlated as part of access entitlements management process to determine the user’s access across the various systems. Often bundled as part of an IGA tool, identity repository offers a consolidated view of identity data. In case of disparate identity repositories, virtualization of identity information is achieved through virtual directories.
- Identity Lifecycle Management: Identity lifecycle management provides the mechanisms for creation, modification and deletion of user identity and associated account information across the target systems and applications. Often referred to as Joiners, Movers and Leavers (JML) process, identity lifecycle management offers inclusive support for all identity related events either through available connectors for automated provisioning/ de-provisioning or use of workflows for manual intervention. Management of user accounts and access entitlements across a multitude of IT systems including cloud-based applications is an increasingly important requirement for identity lifecycle management capability of the IGA tools today.
- Password Management: Self-service password management allows for password resets and user account recovery in case of forgotten passwords on the target systems and applications. Password synchronization ensures that password changes are successfully propagated and committed across all required systems. Progressive IGA vendors offer risk-appropriate identity proofing mechanisms in case of forgotten passwords for account recovery actions, in addition to multiple form factors of user authentication for initiating password changes.
- Access Request Management: The self-service user interface for users to request access to IT assets such as applications, databases and other resources. Access request management encompasses the entire process of delivering a user-friendly approach for requesting the access including searching for and selecting the desired resource from the available resource catalogue to browse the available hierarchy models available in the system and request access cloning. Shopping cart approach for searching and requesting access are becoming increasingly common to deliver better experience for users. Several vendors offer the flexibility of configuring workflows to allow for modification of access requests after the request submission and before actual fulfilment based on business process requirements.
- Policy and Workflow Management: Policy management offers the mechanism to deliver rule-based decision making based on pre-configured rules for identity lifecycle events such as account termination, role modification, exceptional approval, rights delegation and SOD mitigation. The enforcement of policies is either triggered by lifecycle events or determined by associated workflows. Workflow management is concerned with defining the necessary actions to be undertaken in support of a successful event execution or decision-making process. This includes orchestration of tasks involved in the overall decision-making process to support the business requirements. Workflow management should allow for easy customizations to include common business scenarios such as approval delegations and escalations.
- Role Management: Role management delivers capabilities for managing access entitlements by grouping them based on relevant access patterns to improve administrative efficiency. The roles can be defined at several levels, most common being people, resource and application levels. The access patterns for logical grouping of entitlements can be derived with support of role mining capabilities of IGA tools delivered as part of role management. Role governance, a critical capability within broader Access Governance, encompasses basic role management as part of the overall role lifecycle management.
Access Governance:
- Identity Analytics: Identity analytics uses data analytic techniques to derive meaningful information out of the enormous logging and auditing information generated by the systems with an objective to enhance the overall efficiency of IGA processes in an organization. This includes recommendations for efficient use of roles, risk-based mitigation of access policy violations, automated access reviews and even correlation of identity events across disparate systems to derive actionable intelligence. Identity analytics is fast becoming an important vehicle to achieve visibility into the operational state of IGA processes by analyzing the operational data generated by IGA tools to evaluate process maturity and adherence to service quality standards as well as compliance mandates. Identity analytics also feeds required user access information from authentication and authorization events to User Behavior Analytics (UBA) tools for prototyping user access behavior patterns and detecting anomalous access.
- Access Certification: Another key capability to gain an organization-wide visibility in the state of access across the multitude of devices, systems and applications including access to cloud-based applications. Access certification allows process and role owners to initiate on-demand or periodic access reviews to manage attestations that users only have the access rights necessary to perform their job functions. Access certification campaigns facilitate faster and accurate reviews of access by highlighting policy violations and permission conflicts in users' access entitlements across multiple applications that are to be revoked or approved under listed exceptions. More commonly based on resource level or hierarchy requirements, access certification capabilities are increasingly becoming risk aware to include micro-certifications based on the risk of an identity lifecycle event. Unlike periodic access certifications, event based micro-certifications contribute significantly to continuous Access Governance capabilities of an organization.
- Role Governance: Role governance refers to the capability of having control of and visibility into a role’s entire lifecycle, from its inception to its decommission. In a typical role-based access control (RBAC) setting, role governance monitors and tracks the following key processes for governing the role lifecycle. IGA tools provide varied level of support for governing each of these role lifecycle events:
- Role Definition – Defining a role based on the business functions and logically grouping the access entitlements based on the approved prototypes
- Role Approval – The process of seeking consent of business, process or role owners including appropriate role analysis and tracking of approvals with associated workflows
- Role Creation – Monitoring and auditing of tasks involved in implementation of approved roles in production
- Role Assignment — Performing SOD and other policy checks to ensure role assignment is compliant
- Role Modification — Ensuring that changes made to existing roles are approved, tracked and do not introduce new risks
- Role Optimization — Using intelligence from identity analytics for identifying inefficient use of roles and approval processes and implement measures to optimize roles to improve the efficiency of user access administration.
- SOD Controls Management: SOD Controls Management refers to the controls that are important to identify, track, report and often mitigate SOD policy violations leading to substantial risks of internal fraud in an organization. These controls are essential to manage role-based authorizations across applications with complex authorization model, especially ERP and other complex homegrown applications. Key controls that are offered as part of SOD controls management include cross-system SOD risk analysis, compliant user provisioning, emergency access management, advanced role management, access certifications with SOD analysis, transaction monitoring and auditing and reporting.
- Reporting and Dashboarding: This refers to creation of valuable intelligence in formats that are easily ingestible by business functions for the purposes of enhancing governance and supporting decision making. Reporting is facilitated by in-built reports with provisions provided for customized reporting. Dashboarding is an important auditing control that allows for easy and business-friendly abstraction of metrics and data modelling to monitor effective operation of IGA processes. IGA vendors offer in-built templates for reporting with the ability to customize reporting to suite business’s auditing and reporting objectives. Most vendors allow for IGA data export using specified industry formats into third-party reporting and analytics tools for advanced data modelling and business intelligence. For the purpose of evaluation of reporting and dashboarding capabilities of IGA vendors in this Leadership Compass, besides common reporting using in-built templates, we look at the ability of vendors to provide the breadth and flexibility of data model for customized reporting as well as the dashboarding capability to support complex and granular data metrics for easy interpretations.
Besides the core IGA capabilities described above, we also consider several operational factors in our evaluation of IGA vendors for this Leadership Compass. These operational criteria are:
- User Experience (UX): UX is an important aspect of IGA for security and IAM leaders trying to bridge the gap between the inconvenience of security controls and demand for enhanced user engagement through self-service options. Traditional IGA controls are overladen with several inefficiencies including poor design of user and admin interfaces that prevent easy understanding and completion of common IGA tasks. There is an increased need for organizations to ensure that IGA tools support their UX goals. Most vendors have significantly re-engineered their user interfaces to support better UX, a shopping cart paradigm for requesting access being the most common approach today. Many others are offering mobile support for common IGA tasks such as access requests, password resets and request approvals.
- Automation support: Automation of common IGA tasks has always been a priority for organizations to reduce the inaccuracy and administrative inefficiency encountered by manual completion of IGA tasks in the direction of making IGA operations leaner and achieve lower TCO. Most IGA tools provide support for automated provisioning and fulfilment leading to basic automation of IGA requirements. Some organizations have advanced requirements for automation such as automated access reviews and event-driven access certifications. While some vendors have started to support these capabilities, IAM leaders must ensure the right mix of manual and automated IGA processes to ensure the effectiveness of processes is preserved by continuously monitoring them against defined key performance indicators (KPIs).
- Ease of deployment: A lack of skillset combined with complexity of IGA deployments has led organizations to seek external help and actively engage IAM professional service providers to help with deployments. This can increase the overall TCO of IGA deployments by nearly three folds during the initial years of your IGA deployment. It is important that IGA vendors allow for easy deployment approach for organizations to help manage with available internal resources. Besides underlying software design, IGA products should allow for easy customizations using common scripting languages as well as offer support for configuration and change management. This includes availability of features that help organizations reduce environment-based configurations such as support for DevSecOps and scripted deployments. We also evaluate ease of product upgrades along with the ease of configuring the product for operational requirements such as high availability, automated failover and disaster recovery.
- Third-party Integrations: IGA products are required to integrate with several other enterprise products and applications to deliver the expected business value. Most common integrations with IGA products as evidenced in the market are integrations with:
- IT Service Management (ITSM) tools, primarily ServiceNow, to essentially offer a common front-end for users to request access and other help-desk related tasks
- Enterprise Mobility Management (EMM) tools to make IGA tasks accessible on mobile devices and even extending mobile Single Sign-On to IGA
- Privileged Access Management (PAM) tools to offer emergency access management for complex authorization model applications and for privileged Access Governance
- User Behavior Analytics (UBA) tools to help organizations establish a baseline of user behavior with feeds from identity analytics and detect anomalous behavior.
- Data Access Governance (DAG) tools to extend standard IGA controls to data and information stored across multitude of systems including device endpoints, file shares, network mounts etc.
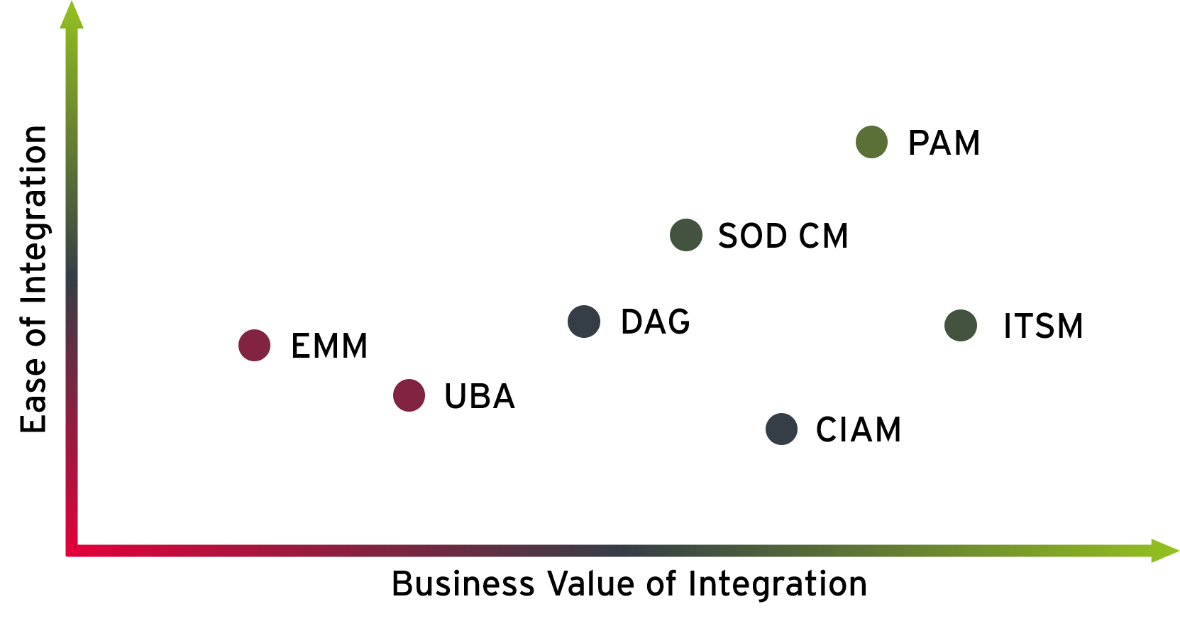
Ease versus perceived business value of IGA integrations with enterprise systems
Scalability and Performance: With an increasing IT landscape for organizations, IGA deployments can easily go under stress to perform better in terms of process execution, target integration as well as overall scalability. IGA products are evaluated based on their ability to scale-up for accommodating an increase in the number of users, identity attributes, roles, managed targets and system connections. Many IGA tools have recently undergone significant product re-architecture to meet the scalability and performance needs of the organizations in a digital era.