What Is Cloud Security?
As more and more organizations use cloud services cyber security and compliance has taken centre stage. The benefits of using the cloud for business-critical applications can be undermined if this leads to cyber-attacks, data breaches and compliance failure.
Let's take the first step on the stairway to cloud security.
Cloud Security Has the Same Objectives
The objectives of cyber security for using cloud services are the same as those for other ways that IT services are delivered:

The approaches to cyber security around cloud services are set out in various standards.
But Responsibility for Security Is Shared
However, the responsibilities for the different aspects and the processes involved are shared between the cloud tenant and the CSP (Cloud service provider). In today’s hybrid IT where some services are delivered through the cloud and some are delivered in other ways – on premises, at the edge and via hosting – this shared responsibility can cause confusion.
This confusion can lead to security weaknesses and provide opportunities for the cyber adversaries as well as leading to failure to comply with regulatory compliance obligations. When using cloud services there are two major security considerations:

The keys to strong security in the hybrid cloud IT environment are:

Cloud Models
There are three different models for cloud services and four ways in which these can be deployed. Let’s look at each of these in more detail.
Cloud Service Models
There are three different models for the kind of cloud services provided and these can be thought of as layers, each providing more business-oriented functionality. The lowest layer IaaS (Infrastructure as a Service) provides basic computing capabilities. PaaS (Platform as a Service) provides the tools and middleware needed to build and deploy business application as managed services. SaaS (Software as a Service) delivers applications ready for the business to use without the need to install, run and manage them.
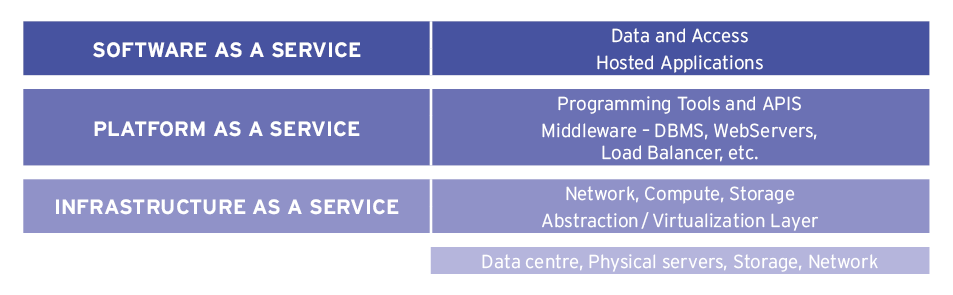
One important point to note from the diagram is that the tenant is always responsible for access to their data and the services that they use.
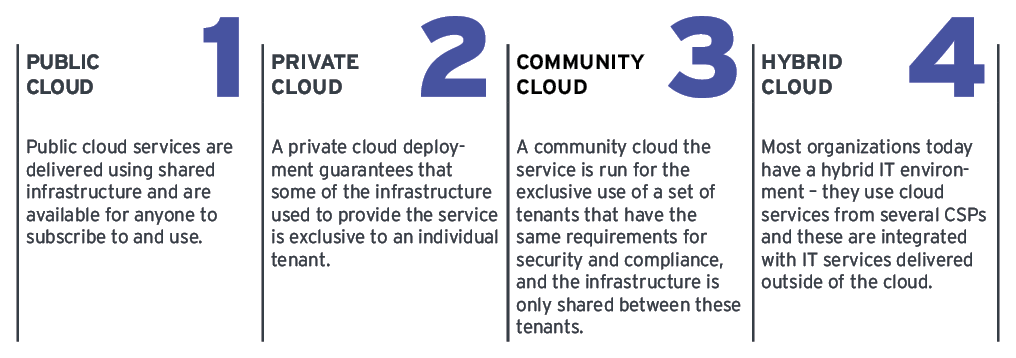
Cloud Deployment Models
There are 4 ways in which these services can be deployed.
Organizations typically, use multiple cloud services from different CSPs including office productivity tools, a CRM system as well as IaaS for test and development.
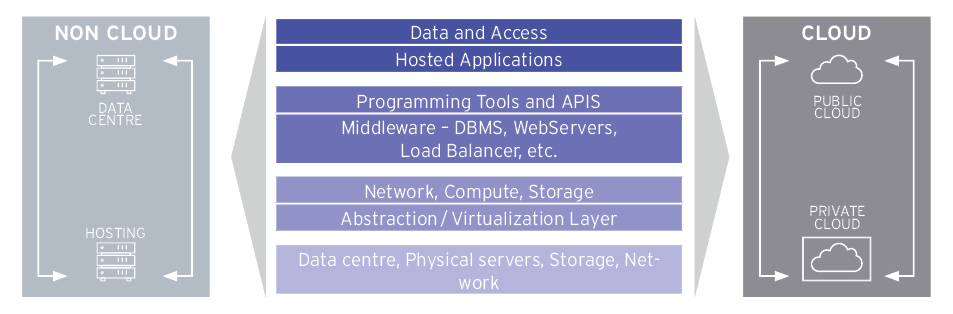
At the same time legacy applications and business critical data remain on premises or in managed hosting. This hybrid multi-cloud environment creates significant challenges relating to the governance, management, security, and compliance of the whole system.
Hybrid IT Needs a Common Security Architecture
What is needed is a consistent approach with common processes supported by a single platform that provides all the necessary functions across all the various components involved in delivering all the services. A blueprint for a hybrid IT security architecture provides this.
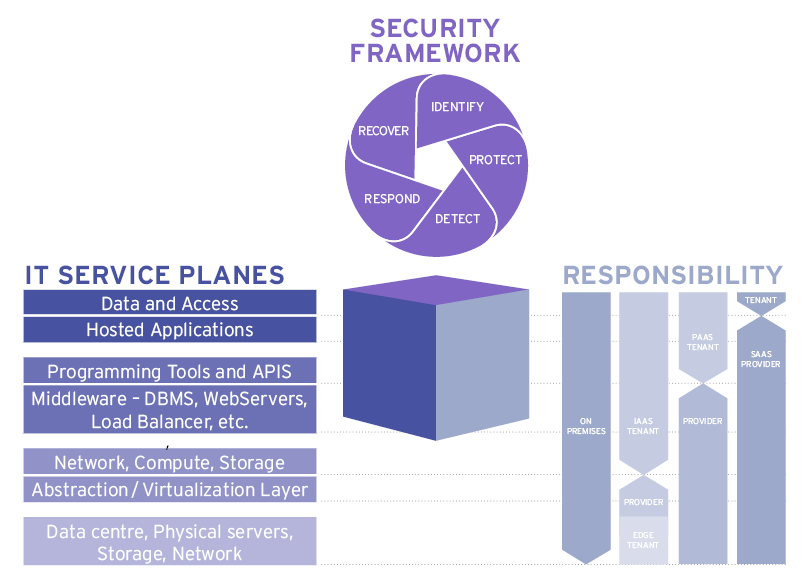
As previously described, there are six distinct planes in the IT service delivery stack. For cloud services some of these planes correspond with the service model (IaaS, PaaS, and SaaS). These all need to be managed and secured for all services. However, the responsibility for managing each plane is split between the tenant and the CSP in a way that depends upon how the service is delivered.
This division of responsibility is illustrated in the figure above. It is important to note that the tenant is always responsible for managing access to the service and the data it contains.
- The lowest plane is the physical service infrastructure which includes as the data centre, the physical network, the physical servers and the storage devices. This is always the responsibility of the CSP in the case of a cloud service.
- The next plane above this is often based on a virtualization or abstraction layer that hides the physical infrastructure from the service user. This provides a set of basic IT services including a network, computing and storage capabilities. This layer corresponds to IaaS and the IaaS customer is responsible for the security of everything above the abstraction layer.
- The next plane above includes the tools and middleware needed to build and deploy business applications. For PaaS (Platform as a Service) these are the responsibility of the CSP.
- Above the middleware are the business applications and for SaaS (Software as a Service) these are the responsibility of the CSP.
- The highest plane is the governance of business data and control of access to the data and applications. This includes security of the endpoints. This is the responsibility of the customer.
Benefits of Using Cloud Services
Businesses rely upon IT services to operate, but the internet has made it possible to get closer to customers and partners. It also supports new ways of doing business. For example, procuring remote access systems to enable remote working is costly and slow, and managing them is complex, but cloud services can solve both challenges.
Challenges of Doing it Yourself
The app on the end user’s mobile device is the visible tip of the digital iceberg. This app has to be supported by data and systems that to allow it to offer a useful service. To offer an item for sale needs a database of what items are available, their prices and where they are located. When an item is put in the bag and purchased the systems need to create workflows for it to be picked, packed, and dispatched.
For the purchase to be completed a financial transaction must take place involving payment card processing as well as tax and accounting processes. All of this takes place in the datacentres providing the IT services behind the app. These datacentres need power and cooling together with network access and strong physical security. The applications need servers and storage devices to be acquired, installed, and set up.
The software and middleware required by the application must be installed and configured. All of this needs to be secured, updated, and maintained. At the end of life, these assets need to be decommissioned and disposed of.
These are significant tasks needing a high level of skill, and the benefits of using a cloud service are that many of these tasks are outsourced to the CSP. While many applications are now essential to the organization the costs of running them in house are too high and the skills needed are too rare especially for smaller organizations. On the other hand, CSPs have the benefits of scale that allow them to reduce costs and keep the skilled personnel needed.
During the 1990s many organizations acquired software that became shelf-ware that was never put into production because its deployment was too complex. SaaS offers an attractive solution to this where the tenant buys a working application that is ready to go from day one.
The tenant does not need to acquire, deploy, or maintain the software or the infrastructure and costs move from capital expenditure to operational costs in terms of a subscription based on what is used.
Fast, Flexible and Functional
The start up with an idea for a new service or product can obtain the infrastructure needed to develop this idea without the need to obtain large amounts of venture capital to fund the infrastructure needed.
It can use a credit card to buy what is needed to develop and try out the idea in the knowledge that if it takes off, capacity can easily be added as needed and paid for by success. Organizations can use cloud services to accelerate their digital transformation in a way that is similar to the start up.
They can experiment with new business ideas and new approaches to software development without the need for procurement delays and capital expenditure. However, the challenge often remains of integrating the new with the old. Many organizations have legacy applications often decades old but upon which the business still depends.
Keeping these running means that the organization needs a data centre with all the fixed costs that this implies. These organizations are faced with the challenge of how to integrate legacy and cloud. One approach favoured by some is application modernization – where the legacy applications are rebuilt using a modern software architecture based on containers.
This may provide future benefits but involves costs and risks and is best based on a clearly articulated business benefit. Another approach is described as lift and shift – where the legacy applications are moved unchanged to a cloud service. This is not as easy as it sounds since the applications often has dependencies on obscure features that are not discovered until after the move.
All approaches lead to questions around security and compliance. The risks and controls in the in-house deployment are known whereas those in the cloud are less certain and this has become a limiting factor for many organizations.
Cloud Risks
There are 3 major business impacts associated with the cybersecurity of using cloud services. These are loss of business continuity, misuse or leakages of data, and failures of compliance. The approach to mitigating these risks is one of good governance that ensures a consistent approach to the security of IT services regardless of how they are delivered.
Risks to Business
The detailed controls depend upon the kind of service being used. Since the responsibility for security and compliance is shared you need to ensure that you meet your obligations and assure that the CSP meets theirs.
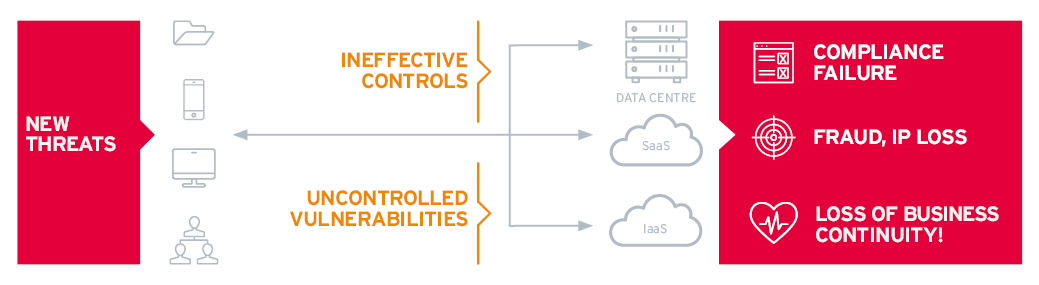
These risks arise for several reasons. The cloud attracts new threats – as cyber adversaries exploit the opportunities provided through the growing use of these services. Confusion by tenants over how responsibilities for security and compliance are shared together with poorly managed control over their use of these services. In addition, many tenants fail to adapt or apply their normal internal controls, such as identity and access governance and vulnerability management within the services.
Compliance Failure
Many organizations have invested heavily to ensure compliance with the laws and regulations that are relevant to their business. However, the cloud service itself may not be compliant with the necessary regulations or the tenant may not implement the necessary controls. Employees and associates can use personal cloud services to perform their jobs without reference to their employer.
The increasing number of laws and regulations relating to the processing of personal data such as GDPR and CCPA add to these challenges.
Business Continuity
There are several ways in which the use of cloud services could impact on business continuity. Data held in cloud services may be subject to ransomware attacks and the tenant’s use of the service may be subject to denial-of-service attacks like DDoS. Natural disasters may also impact datacentres, communications, or power.
In addition, there is a risk of lock in - cloud services are often based on a proprietary technical architecture which can make it very difficult to migrate to another provider. The use of a cloud service depends upon the end-to-end availability of resources and organizations must take this into account in their business continuity plans.
Learn how to ensure business continuity for the cloud in the Analyst Chat Podcast. In episode 67 Mike Small joins Matthias Reinwarth to explain why business continuity is essential for cloud services, especially in light of current events.
Data Breaches and Fraud
Using cloud services can make it more difficult to control legitimate access to data and increases the risks of data leakage. The data is potentially at risk while in transit, during storage and while being processed. To perform maintenance the CSP needs access to the service infrastructure, and this may provide access to the tenants’ data. In addition, the CSP may be subject to legally binding requests from the government to disclose data held in the tenants’ accounts.
The tenant’s data within the service is held on physical storage devices which may be reused later by other tenants or discarded at end of life with a risk that the data may leak. End users may store regulated data within the service in a way that breaches compliance obligations.
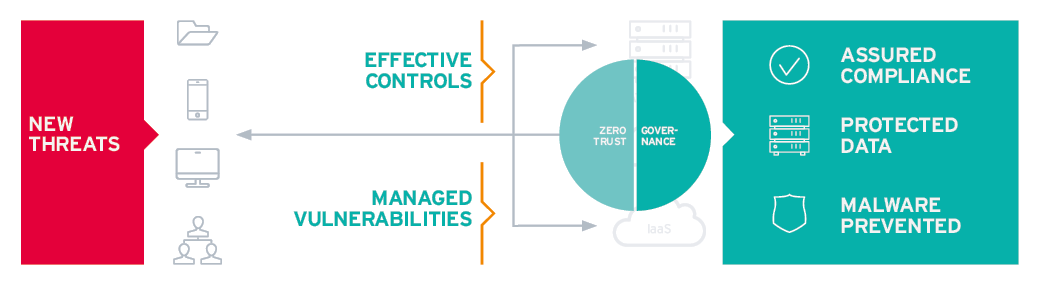
Best Practices to Mitigate Cloud Risks
There are two major approaches to mitigating these risks – control over how you use the cloud and governance of the cloud services you use. Be absolutely clear over how responsibility is shared between you and the CSP. Ensure that you meet your part of the bargain and assure that the CSP meets theirs.
Be Prepared
The organization itself needs to be ready to use cloud services; success starts with mature internal IT governance processes. There must be a robust process for procuring cloud services that should be easy to use so that it is not bypassed by line of business managers. Not all risks are equal – this procurement process must prioritize which risks are important and specify the controls needed to manage these.
The cloud service tenant must ensure that the controls for which it is responsible are properly implemented. Since the delivery of the cloud service is outside the direct control of the tenant, it must assure that the service is delivered securely to the agreed specification.
Take a Risk Based Approach
Tenants should take a risk-based approach to the use of cloud service. It is only by understanding the precise risks that are relevant to your use can you specify the appropriate controls that are needed. there are several existing frameworks for the best practices around IT Management including: ISO/IEC 20000, ITIL and COBIT5.
Organizations should adopt one of these.
You should assure that the CSP implements the controls that are relevant through independent certification that they are designed, built, and operated according to security best practices.
Include Cloud in Business Continuity Plans
Although cloud services claim to be more resilient than in-house systems most do not claim 100% availability. Therefore, it is essential to include cloud use in business continuity plans. Furthermore, the use of the services necessarily involves multiple pieces of infrastructure such as networks and in-house equipment as well as end user devices.
This makes it essential that the end-to-end components are included as well.
Zero Trust Access Controls
CASBs (Cloud Access Security Brokers) address many of these challenges by providing visibility of use and control over access to cloud services by organizational users. However, while this is important more is needed to cover all the risks.
CASB solutions have evolved to become an essential component of an integrated approach to cloud security. These are expected to include CASB, Cloud Security Posture Management (CSPM), Data and User Protection, SWG (Secure Web Gateways), and Zero Trust Network Controls to provide a complete cloud security solution.
Manage Your Cloud Security Posture
Cloud services themselves now feature extensive capabilities for the tenant to use them securely. However, these capabilities are often not used or are not used correctly. The risks associated with organizational use of cloud services often stem from misconfigurations that leave vulnerabilities which can be exploited by cyber adversaries. To counter these risks, CSPM (Cloud Security Posture Management) functionality to detect, report and remediate these is now expected.
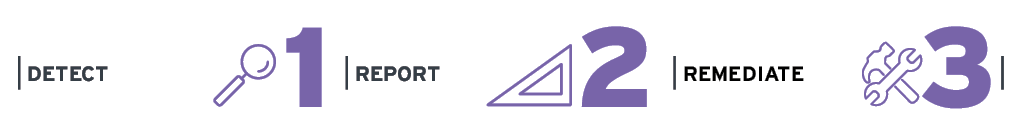
CASBs have traditionally focussed on controlling user access to SaaS services and the protection of unstructured data. However, IaaS is increasingly being used to deliver business transformation through new and modernised business applications, CSPM is important to manage the risks from this.
Cloud Security Vendors
Cloud services provide assurance of the level of security of their clouds. They also provide tools and capabilities for the tenants to use the services securely. Most security tool vendors now provide variants that are relevant to the cloud, often offered on the cloud marketplaces. A comparison of the major IaaS Providers can be found here.
Cloud Identity and Access Control
Cloud services must as a minimum provide assurances over how they secure the infrastructure as well as capabilities to authenticate the tenants’ users, and control access to the tenants’ resources held in the service. Identity as a Service (IDaaS) is fast becoming the new face of Identity and Access Management (IAM) with several vendors now delivering cloud based IAM services to support the growth in cloud-based applications in the enterprise.
Microsoft Office 365 provides controls through Microsoft Azure and Google’s Cloud Identity provides access to many popular cloud applications and offers some endpoint management features. Here is an example of the identity and access governance capabilities provided by SAP.
To manage and control access to SaaS clouds CASBs are an important tool. These provide visibility over which clouds are being used and what data is being held. A comparison of CASB’s from a range of vendors can be found here. Most of these vendors also provide CSPM solutions either integrated into or as standalone options.
In episode 36 of the Analyst Chat Podcast: Questions to Ask Your Cloud Provider About Security Alexei Balaganski and Matthias Reinwarth discuss the security challenges for enterprises moving to the cloud and explain why security in the cloud is still your responsibility.
Secure Access Service Edge
There is also a growing market for the so-called SASE (Secure Access Service Edge) tools. SASE is the convergence of wide area networking, or WAN, and network security services like CASB, FWaaS and Zero Trust, into a single, cloud-delivered service model. The objective of this being to secure access to the services.
Cloud Backup and Disaster Recovery
One area often forgotten is back up and recovery of tenants’ data. It is often assumed that this is included in the service. This is a false assumption, for example most cloud storage systems provide limited recovery of data legitimately deleted by the tenant. So, cloud data protection solutions are usually needed to provide data backup and recovery capabilities.
How to Find the Right Cloud Security Solution
KuppingerCole provide a range of Buyer’s Compass reports to help organizations choose the right solution for their particular circumstances. These reports provide information about Use Cases, Functional Selection Criteria, Non-functional Selection Criteria, Technical Prerequisites, Organizational Prerequisites and Questions to ask the vendors.
Hybrid Security Buyers’ Guide
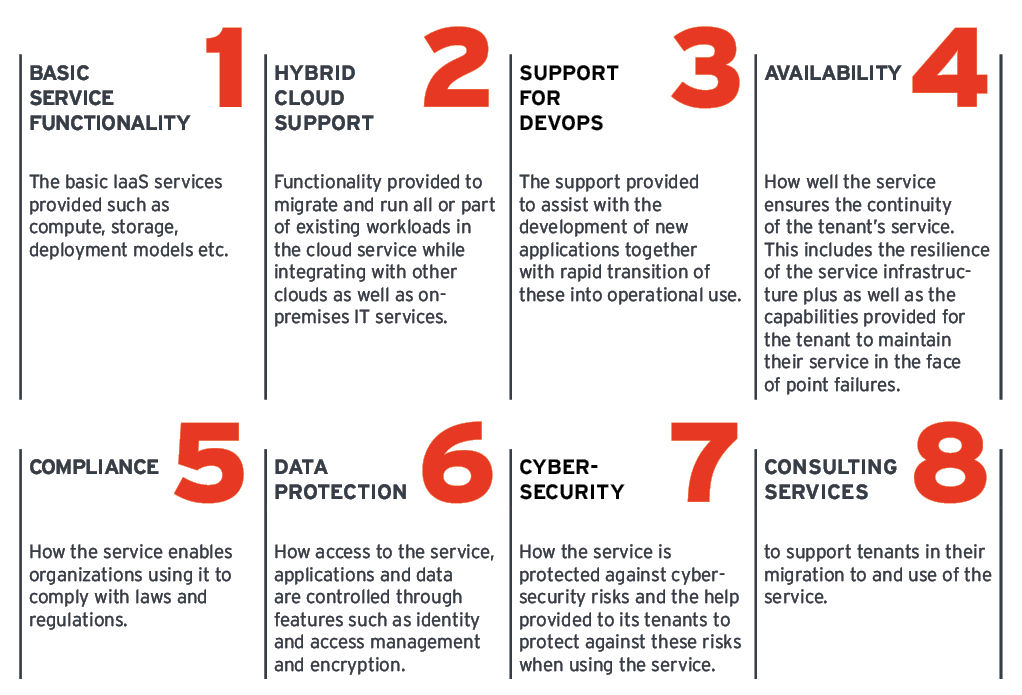
Organizations now commonly use multiple cloud services as well as on premises IT. This KuppingerCole Buyer’s Guide focusses on IaaS services. It will provide you with questions to ask vendors, criteria to select your vendor, and the requirements for successful deployments.
This report will prepare your organization to conduct RFIs and RFPs for IaaS as part of a Hybrid IT service delivery model. The core features and functionalities for that need to be evaluated for IaaS include:
The Future of Cloud Security
The market for cloud services is forecast to grow significantly over the next five years. Much of this growth will depend upon organizations moving, migrating, or modernizing existing workloads. While according to estimates from IBM the potential market over the next 5 years is over $1 Trillion currently only around 4% of enterprise workloads have been moved to the public cloud.
Security and Compliance Are the Limiting Factors
The factors limiting this are management, security, and compliance. Therefore, to realise this potential it is essential that these factors are addressed. In response to these challenges, software solutions such as CSPM, and managed services have emerged. In addition, CSPs are including capabilities within their platforms.
CSPs Need to Respond to Tenant Needs
To enable this growth CSPs will need to provide greater transparency of the existence and effectiveness of their controls to support the take up by the highly regulated industries such as finance. Organizations need an integrated view of their security and compliance posture. To achieve this much greater integration is needed between the controls provided by and within the cloud service and the organizational GRC tools.
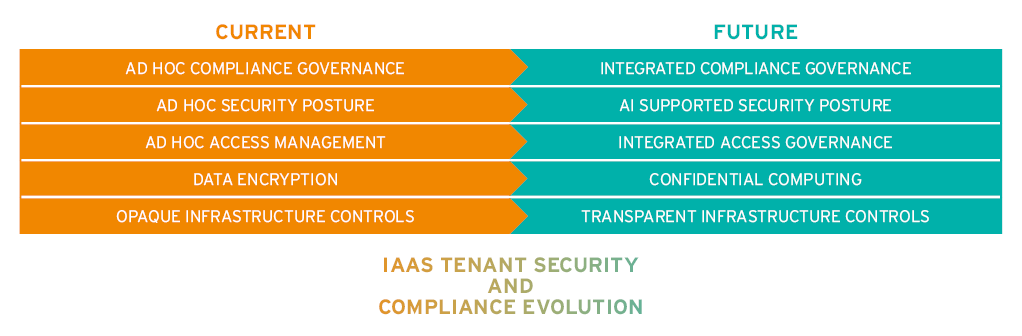
Another challenge is overcoming concerns related to legal requests from governments to turn over or intercept tenant data. Contractual solutions to this are not sufficient and services will need to offer technical controls for confidential computing. As well as providing tools for the tenant to use and develop applications using Artificial Intelligence / Machine Learning cloud service vendors will increasingly offer capabilities that exploit these capabilities to improve the tenant’s security and compliance posture.
Some CSPs are already including these capabilities within their services a notable example being Oracle Autonomous Database. This claims to automatically patch, tune and secure systems. Machine Learning systems are ideally suited to the tasks of systems management where there are clear rules and well-defined environments.


















































