Some weeks ago I stumbled upon an article, which said that the MDM (Mobile Device Management) market will grow massively within the next five years. I don’t doubt that the market will grow. However I’d raise the question whether it should grow that much – or, in other words, whether MDM is really the solution of choice. I don’t doubt that there is some need for MDM technologies. However, this might be more about understanding MDM as an element of other technologies or a tactical piece of a bigger puzzle.
Let me explain why.
The problem organizations are facing today is that there are more users, more types of devices, and more deployment models they have to deal with. They need to give their users access to the information they need (and thus the information systems they need), regardless of the device and the deployment models – but with enforcing information security and regulatory compliance. It is about the impact Cloud Computing, Mobile Computing, and Social Computing have and how to deal with it in a secure and compliant manner.
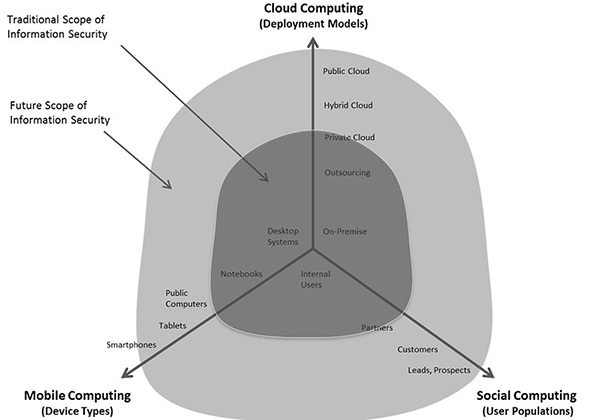
This “Computing Troika” means that we have to strategically change the way we are dealing with identities and access. We have more identities and we have to support more ways of gaining access – to resources which are sprawled across multiple deployment models.
Notably, this is not only about users with smartphones or tablets, the devices primarily in scope of MDM technologies (even while some grow beyond that to Microsoft Windows 8 or Apple OS X support). It is about a multitude of devices, from the classical desktop PC in the company, in the home office, or in an Internet Café; it is about notebooks of employees and all the different types of externals; it is about all the smartphones, tablets, and potentially devices we cannot even imagine today. And I’m not even speaking about the Internet of Things and M2M (machine-to-machine) here, which also is about some identities requiring access.
Can we solve this by managing mobile devices? Obviously, that can help. But it is far away from solving the strategic challenge. Furthermore, any approach which focuses on disparate management of a group of devices is questionable. Why not focusing on the solutions which help managing all types of devices, including the “traditional” ones?
Obviously, a device-centric strategy and differentiating between some different types of devices is not sufficient to solve the challenges of today. The same is true for network-centric approaches – if there is not *the* perimeter anymore, protection focusing on that perimeter is insufficient.
The future is about understanding the risk of information access and comparing it with the risk of the access request. The risk of the access request is based on the context, a topic my colleague Dave Kearns focused on at his EIC keynote some four years ago. Context is about the device, the location, the type and strength of authentication, the role of the user and thus also its relationship to the organization, the health status of the device, and many other aspects. If there is sort of a positive balance of information risk and access risk – fine. If not, the access risk either can be mitigated, for example by step-up authentication, or the access might be refused or at least limited.
That requires technologies like versatile authentication, risk-/context-based authentication and authorization, and Dynamic Authorization Management. The latter is required to enable applications to do dynamic authorizations based on policies and on the context, instead of hard-coding authorization rules or at best relying on coarse-grain decisions. It is about putting a risk- and context-aware approach to information security at the centre, instead of artificially protecting devices (instead of information) or perimeters.
MDM might help in mitigating risks for some devices. So it is a concept within that bigger picture. However, without understanding the bigger picture and addressing this, MDM is more sort of an alibi than a real solution. Furthermore, MDM in that bigger picture and with all the devices in mind which can be used to access corporate information (systems), there is a good reason to look for solutions which integrate MDM into a bigger scope – like Client Lifecycle Management solutions which manage all types of devices.
Nevertheless, the MDM market will grow for some time. However, it also will change, maybe quicker than many expect today. And, most important, there are other technical building blocks you should look at first, to address the cause and not the symptom.


















































