KuppingerCole's Advisory stands out due to our regular communication with vendors and key clients, providing us with in-depth insight into the issues and knowledge required to address real-world challenges.


Unlock the power of industry-leading insights and expertise. Gain access to our extensive knowledge base, vibrant community, and tailored analyst sessions—all designed to keep you at the forefront of identity security.
Get instant access to our complete research library.
Access essential knowledge at your fingertips with KuppingerCole's extensive resources. From in-depth reports to concise one-pagers, leverage our complete security library to inform strategy and drive innovation.
Get instant access to our complete research library.
Gain access to comprehensive resources, personalized analyst consultations, and exclusive events – all designed to enhance your decision-making capabilities and industry connections.
Get instant access to our complete research library.
Gain a true partner to drive transformative initiatives. Access comprehensive resources, tailored expert guidance, and networking opportunities.
Get instant access to our complete research library.
Optimize your decision-making process with the most comprehensive and up-to-date market data available.
Compare solution offerings and follow predefined best practices or adapt them to the individual requirements of your company.
Configure your individual requirements to discover the ideal solution for your business.

Meet our team of analysts and advisors who are highly skilled and experienced professionals dedicated to helping you make informed decisions and achieve your goals.

Meet our business team committed to helping you achieve success. We understand that running a business can be challenging, but with the right team in your corner, anything is possible.
Zero Trust has seen a steep increase in popularity over the past few years. While the idea and value of Zero Trust are widely accepted, most organizations still struggle to implement a Zero Trust model across cybersecurity and IAM (Identity and Access Management). The main reasons for that are the inherent complexity of a model that affects all areas of cybersecurity and the gap between an abstract concept of “don’t trust, always verify” and the practical implementation.
The gap between an abstract paradigm and concrete implementation is huge for Zero Trust. Putting Zero Trust in practice requires the right type of services and support.
Zero Trust affects various domains that are commonly split across multiple departments and sometimes even under split leadership. Ownership for Zero Trust must be unified and integration and collaboration between the various parties must be fostered.
Implementations best start at the beginning of the user journey: Authentication. This is the first verification event, followed by device verification and security, network security, and authorization. With the ubiquitous relevance of IAM for authentication and authorization, but also the management of identities, device bindings to users, and management of access entitlements, IAM takes a central role within Zero Trust.
With the inherent complexity of Zero Trust, organizations are well-advised to build on partners that bring experience, proven methods, and the ability to support along the entire Zero Trust journey, from concepts to implementation and operations.
Providers that offer the full range of services from consulting to managed services for support and operations, continuous improvements and evolution of the infrastructure are an interesting option for making Zero Trust initiatives succeed, helping in tackling the complexity with standardized methodology and services. This applies to all sizes of organizations, given that neither skills nor capacity commonly are available at the extent a journey such as the one towards Zero Trust in practice require.
Zero Trust requires defined leadership and an integrated organization where various groups work jointly and collaboratively on a common goal.
IAM is the logical starting point for the Zero Trust journey, with authentication being the first verification of users.
The complexity of Zero Trust mandates that standardized and proven methods and concepts are utilized, building on experience, and leveraging the benefits of the economies of scale. Managed services are a logical choice.
iC Consult can build on their rich experience in delivering IAM managed services to also support organizations on their Zero Trust journey.
Leadership and organization for Zero Trust implementation
Success in Zero Trust requires strong leadership. CISOs most commonly are the ones in charge of the Zero Trust program. They must unite their teams for a joint initiative.
While Zero Trust is not a new topic in IT, it has been facing a massive increase in attention over the past three years. With the pandemic and the rapid adoption of WfA (Work from Anywhere), the pressure on IT to adapt Zero Trust concepts increased massively. However, many organizations are still stuck in the conceptual stage.
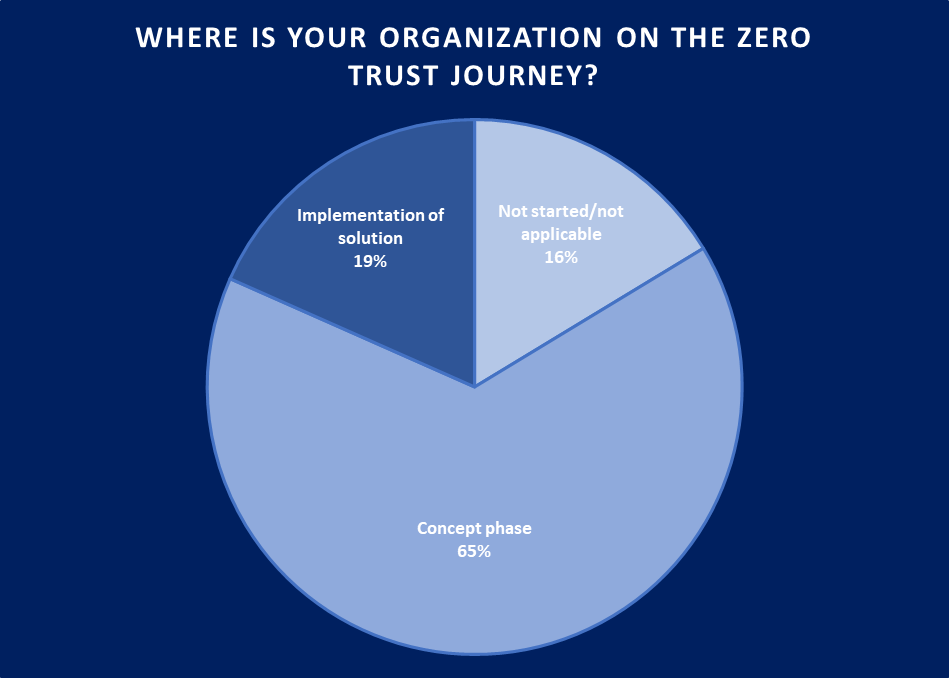
Figure 1: Adoption of Zero Trust is still staggering, due to the complexity of changing IT infrastructures and the gap between concepts and practical implementation (Source: KuppingerCole Analysts)
Only 19% of the respondents to a recent poll conducted by KuppingerCole Analysts are already concretely implementing a Zero Trust approach across their IT and their cybersecurity infrastructure, while two out of three still are in the concept phase. This also explains some growing frustration regarding Zero Trust: While the concept is meaningful, it is a journey to make Zero Trust a reality for a modern cybersecurity infrastructure, helping to strengthen the security posture of organizations.
There are multiple aspects that impact the success of a Zero Trust journey:
While leadership and organization always depend on the state of organizations, the most common approach nowadays is having the CISO in lead of the Zero Trust initiative. In most organizations, CISOs are already responsible for not just “core” cybersecurity including network security, but also for IAM as one of the cornerstones of any Zero Trust approach.
With CISOs nowadays commonly being responsible for both cybersecurity and IAM, they are the best choice for Zero Trust leadership.
When taking a broad perspective on Zero Trust, which is strongly recommended, there are other teams that also must become involved. Aside from data security/governance and software security that already have been mentioned, this affects teams that are responsible for FRIP (Fraud Reduction Intelligence Platforms) and frequently also the network teams, due to themes such as SD-WAN, microsegmentation, and others that are affecting both network security and network infrastructure.