1 Introduction
Identity and Access Management (IAM) has been an integral part of IT security and computing in general for decades. The earliest IAM solutions were often built directly into applications, which created difficulties for organizations to manage. Dedicated, independent IAM systems began to emerge in the 1990s, generally constructed upon common user databases (based on the Lightweight Directory Access Protocol, or LDAP). This enabled organizations to simplify user account creation and maintenance.
These traditional IAM systems were designed to provision, authenticate, authorize, and store information about employee users. User accounts are defined; users are assigned to groups; users receive role or attribute information from an authoritative source, commonly at the employee or contractor onboarding phase. Traditional workforce-facing IAM systems are generally deployed in an inward-facing way to serve a single enterprise.
Starting in the early to mid 2000s, many enterprises found it necessary to also store information about their business partners, suppliers, and customers in their own enterprise IAM systems, as collaborative development and e-commerce needs dictated. Many organizations have built extensive identity federations to allow users from other domains to get authenticated and authorized to external resources.
By the late 2000s and early 2010s, consumer-facing enterprises began deploying separate instances of their IAM systems to house user accounts specifically for those consumer end-users. The types of information that can be obtained from and used in servicing consumer users can be quite different in nature and storage type requirements than those of enterprise workforce users. For example, organizations may want to collect information about other digital accounts a given consumer has, their demographic information, likes and preferences for consumer products, browsing and purchase histories, etc., as well as consumer generated content such as photos and videos.
The processes by which consumer and customer identities are created and maintained also differ significantly in many cases from those used for employee onboarding. Employees usually have digital accounts created for them soon after hiring in the onboarding process. Employees will be assigned to groups from which flow access entitlements. Human Resource (HR) departments validate employee identity documents and populate the user directory with relatively high assurance identity data.
Consumers and customers instead arrive at business web properties and must register for better, more personalized service. Guest checkouts which did not require registration were common in the early days of e-commerce, but as e-commerce grew, companies realized that digital identity has many benefits to offer. For the consumer or customer, registration allows personalization, including features such as retaining history of purchases to make repeat buying easier, and provides messaging options for interacting with brands of their choice. Most customers create accounts with email addresses (and passwords) or use social network login credentials. CIAM platforms have moved to accommodate many different privacy regulations globally, by offering consumer or customer users the facility to view, grant, and revoke consent for the use of their personal information.
For businesses, CIAM solutions are the means by which they can improve customer experiences through personalization. CIAM systems are also repositories of consumer identity, and browsing and purchasing information, which are valuable for organizations that are looking to maximize marketing potentials and revenue.
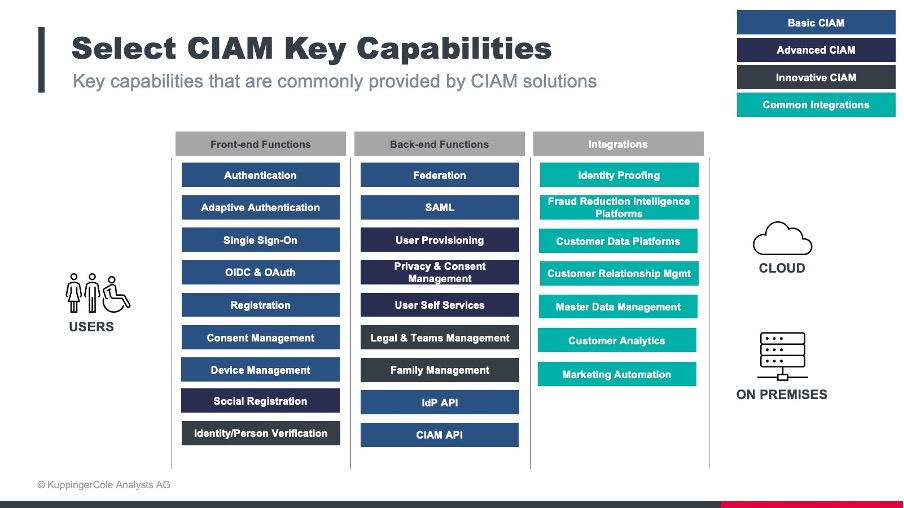
Figure 1: Selection of key capabilities for CIAM solutions
CIAM solutions allow users to associate devices and other digital identities with primary accounts, authenticate, authorize, collect, and store information about consumers from across many domains. Information collected about consumers can be used for many different purposes, such as authorization to resources or for transaction, or for analysis to support marketing campaigns, or Know Your Customer (KYC) and Anti-Money Laundering (AML) regulatory compliance. Moreover, CIAM systems must be able to manage many millions to even billions of identities, and process potentially tens of billions of logins and other transactions per day. SaaS delivery of CIAM services is the norm and will remain so.
CIAM systems can aid in other types of regulatory compliance. Many governments around the world have enacted privacy regulations that empower citizens and residents to control what kinds of information organizations can collect, how it can be obtained, how it must be treated, and how it must be dispositioned upon consumer request. Many CIAM solutions provide these capabilities, plus offer consumers dashboards to manage their information sharing and management choices. Moreover, CIAM systems can help corporate customers implement consistent privacy policies and provide the means to notify users when terms change and then collect acknowledgement.
Improving the consumer experience is often a key goal in deploying or upgrading CIAM solutions. With the increasing digitization of Business-to-Consumer (B2C) interactions, consumers are asked to create and use more and more accounts and passwords. Managing the escalating numbers of digital accounts can be burdensome for consumers if the CIAM systems with which they are engaging are not optimally designed, implemented, and continuously tuned.


















































