1 Introduction
As modern businesses across all verticals continue their rapid digitalization, the need to store, process and exchange data securely is becoming an essential factor for any company. This results from a wide range of challenges: Regulatory and legal requirements, business continuity, data protection for employees and customer and especially the increasing demand for the protection of intellectual property.
At the same time, virtually all companies are refactoring their infrastructures in many application areas, opting to use cloud infrastructures. The collective knowledge of companies 20 years ago was typically stored in internal databases. Today, however, it is distributed across cloud services as diverse as Teams, Office 365, git, Jira or ServiceNow, while earlier on-premises systems are hosted in the cloud on Infrastructure as a Service (IaaS).
Cloud services offer many benefits, including the ability to meet changing demands and the flexibility to deliver new business solutions faster. This applies in particular to the critical areas of communication, all types of workflows, and the exchange of documents including collaboration. Office 365 and Teams as Software as a Service (SaaS) offerings from Microsoft are the tool of choice in many organizations and industries for office collaboration, daily document work, and information exchange with extended supply chains and partners.
Business boundaries are dissolving as the requirements and the ability to share information continuously increase. The trend is clearly shifting towards multi-cloud and hybrid environments, while communication and document exchange in these systems form the basis of essential business processes. These factors pose significant challenges to information security, regulatory compliance, data protection and the protection of intellectual property.
Without assuming from the outset that providers of cloud computing services are fundamentally untrustworthy, a cloud must nevertheless be assessed as "not trustworthy" in the terms of a risk assessment. Data protection can be passively or covertly compromised. Possible malicious actions can be performed from inside the cloud by a malicious administrator or employee. And without going into too much detail here, the national jurisdiction of some states is currently a particular challenge in international interplay, as state bodies are to be granted extensive access to data in cloud infrastructures under the justification of legitimate criminal prosecution.
Without further protective measures, this opens undreamt-of possibilities to obtain access to information that is to be regarded as internal and secret and which, from the point of view of the data owner, must be protected against such scrutiny.
Assuming the trend towards cloud infrastructures continues unabated, traditional cybersecurity approaches that protect infrastructure and systems are no longer appropriate. Traditional cybersecurity typically focuses on protecting networks, systems, applications, servers and endpoints in general. In today's infrastructures, such measures no longer cover central protection requirements in a meaningful way. The question of how to secure data in an increasingly perimeter-less IT between on-premises environments, the cloud and anywhere in between is getting more and more important. As a result of this, today’s cybersecurity is undergoing substantial changes. This calls for a comprehensive paradigm shift, because infrastructures that are neither self-operated nor managed cannot be adequately protected. Instead, the focus is on the data itself, i.e. the payload, so that the infrastructure processing it becomes irrelevant from a data security perspective. As a premise, this infrastructure is postulated as potentially compromised, dangerous and populated by actors to be regarded as hostile, so the information itself must be technically and conceptually safeguarded even in this insecure environment.
At the same time, it must be ensured that no significant loss of functionality occurs. If data security leads to the fact that comprehensive features such as the collaborative processing of documents or even just the basic search within data are no longer possible, this renders the use of modern collaboration platforms pointless. The crucial challenge is to provide the highest level of security without compromising the usability of applications.
Key strategies for data-centric security include the avoidance/reduction of data in the actual cloud systems and a comprehensive approach towards encryption and obfuscation that ensures that encrypted data cannot be restored to its original form by unauthorized persons under any circumstances.
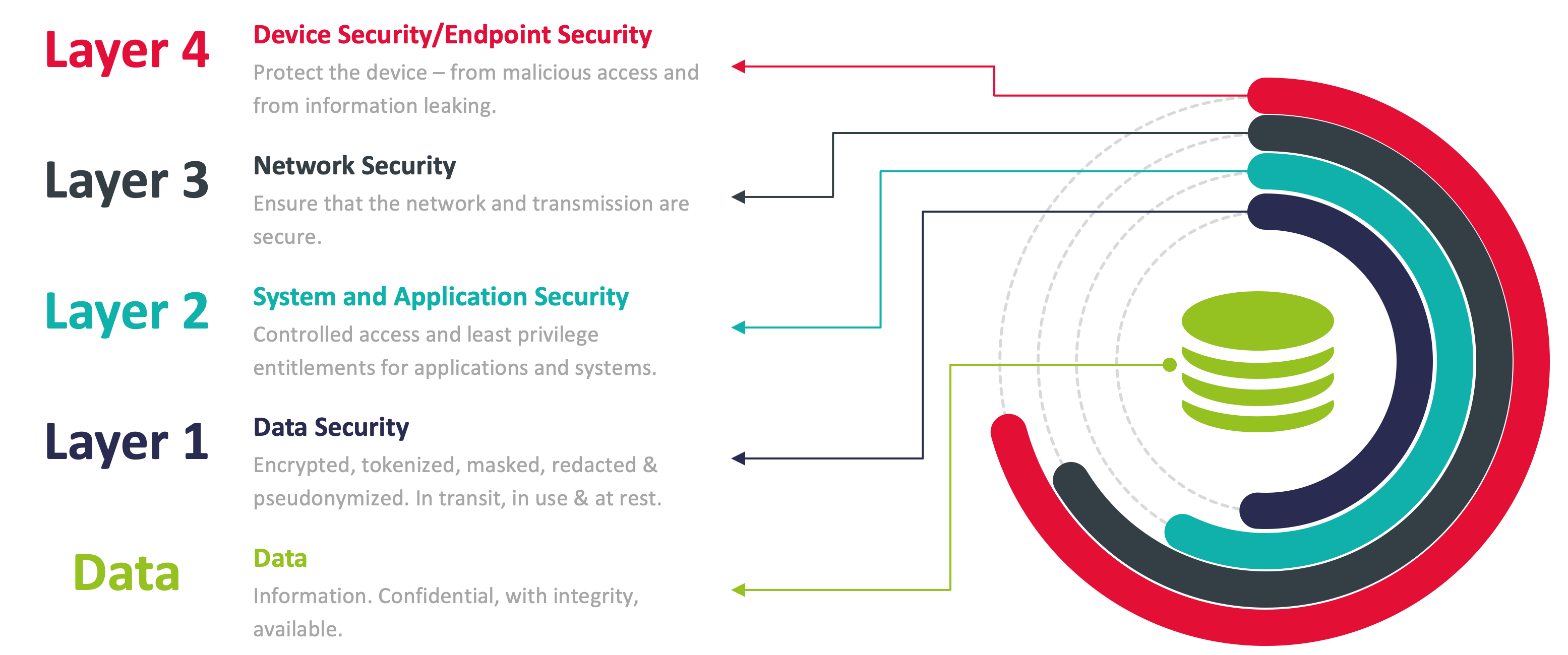
That does not mean that data-centric security is the single, new solution to security challenges replacing everything that has been done before. Data-centric security protects what really needs to be protected, which is the actual information as the payload. Other tiers can be added as part of a multi-layered security approach that covers multiple dimensions of cybersecurity. System and application security, network security and the protection of the user's device/endpoint remain important layers of protection, as traditional security mechanisms (e.g. firewalls or endpoint security) continue to provide additional layers of protection that must first be overcome, safeguarding individual aspects and security dimensions, especially in hybrid environments.














































