1 Introduction
Privileged Access Management (PAM), over the last few years, has become one of the most relevant areas of Cyber Security closely associated with Identity and Access Management technologies that deal with facilitating, securing and managing privileged access for both IT administrators and business users across an organization’s IT environment.
Privileged shared accounts access to cloud and web applications is a broad attack surface that lacks the fundamental strong multi-factor authentication security principle. Cloud administrators and privileged business users become frequent targets for cyber-attacks as they have broad and often unlimited access to a range of management consoles, mission critical SaaS applications, shared corporate social media accounts as well as DevOps consoles.
At KuppingerCole, we define PAM solutions to constitute of the following key tools and technologies:
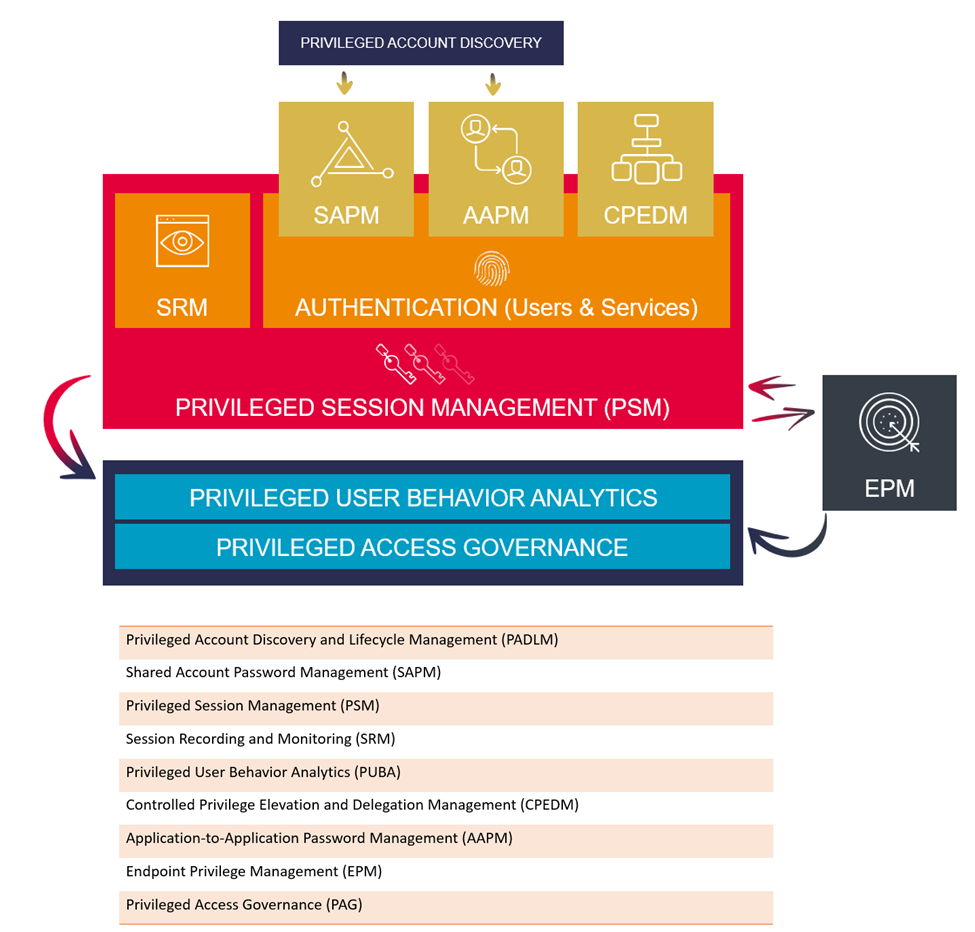
Of the available Privileged Access Management (PAM) technologies, PSM remains one of the three core technologies that constitute a baseline PAM solution, the two others being Shared Account Password Management (SAPM) and Controlled Privileged Elevation and Delegation Management (CPEDM). PSM is also one of the most sought-after security capabilities by security leaders to gain visibility and control over privileged activities in their IT environment that is consistent with the organization’s security policies and regulatory regimes.
Privileged Session Management (PSM) technologies have existed as point solutions for years before they started to amalgamate within PAM tools to solve broader privileged access management use-cases beyond the common remote access use-cases. Today, PAM tools depend entirely on PSM technologies to establish, secure and control administrative access to the range of IT systems and applications in a hybrid IT environment. These capabilities, however, have predominantly been marked by the need to manage privileged session activities to address the wide range of operational, security and regulatory requirements for organizations across the industry verticals.
PSM technology primarily addresses these challenges for an organization’s IT management:
- Exposure of the sensitive credentials to users and devices that may be easily compromised
- Lack of operational visibility and control over (outsourced) IT operations on critical systems and applications
- Lack of auditing and monitoring of privileged activities
- Lack of forensic investigation capabilities
And PSM tools essentially offer the following features to address the challenges noted above:
- Secure and isolate session establishment to target systems including user authentication and role-based authorization by preventing privileged credentials being exposed to users as well as devices
- Session management including Single Sign-On
- Controlled access (Time based access, command control, session termination etc.)
- Privileged session recording and play-back
- Real-time session monitoring, alerting and response
- Forensic investigation capabilities
IT infrastructure, operations, and security leaders are under increased business and regulatory pressure to assess and manage the security risks arising from increased cloud access patterns of IT administrators, third-party vendors and privileged business users. To meet the security requirements of increased cloud adoption, PSM technology over the past few years has undergone a major transformation of its on-premises only approach to include the emerging privileged access patterns of an increasing cloud-dominated IT environment. PAM vendors are continuously adding native cloud-ready features to their PSM technology in order to address the security risks of administrative access to cloud platforms and services. CyberArk Privileged Session Manager for Cloud offers a unified approach that not only supports multiple cloud platforms and web-based applications, but also enhances the ‘ease of access’ factor while securing the privileged access to cloud environment.
In this Executive View, we discuss CyberArk’s session management capabilities for cloud admins and privileged business users to manage privileged access to cloud infrastructure and applications (IaaS, PaaS and SaaS) via CyberArk Privileged Session Manager for Cloud. We also discuss how the acquisition of Vaultive technology strengthens CyberArk’s Privileged Session Manager capabilities to deliver a unified set of security controls across an organization’s hybrid environment.


















































